- Compare Editions
- Product Information
- Resources
- Licensing / Pricing
- Support
- Contact
Back to Setup Guide for Ransomware Protection
Some customers have come up with their own mitigation techniques during a ransomware attack. These might involve removing user rights from directories, forcing a logout of a user account, etc.
To run an external program as an action in response to the monitor detecting active ransomware activity, use the Start Application action.
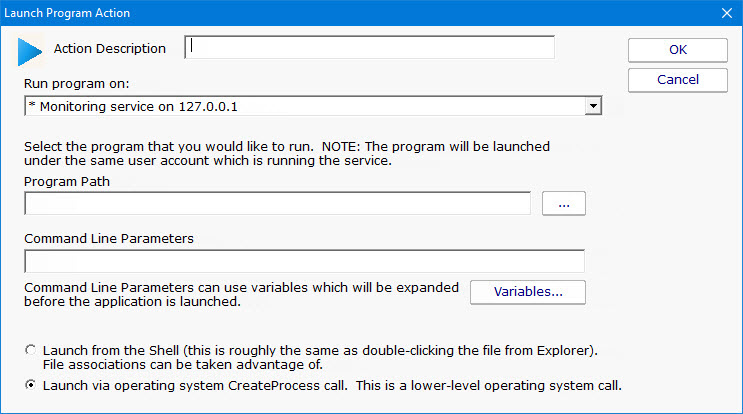
IMPORTANT: When setting up the Start Application action it is important to pay attention to where the application/program is going to be run. This is shown near the top of the action configuration dialog.
“I have been using PA Server Monitor for almost 8 years in some way, shape, or form. It's the best tool I've used.”
Chris N., ChrisComputing.com, USA