- Compare Editions
- Product Information
- Resources
- Licensing / Pricing
- Support
- Contact
Back to Setup Guide for Ransomware Protection
This is PA File Sight's strongest detection method. It requires a feature that is only available in the Ultra edition of the product (the User Activities tab).
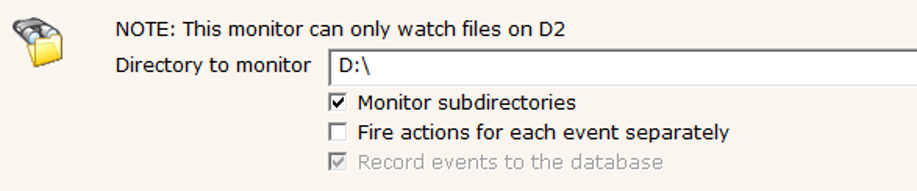
To set it up, create a new File Sight monitor, and enter the path to monitor, as shown below:
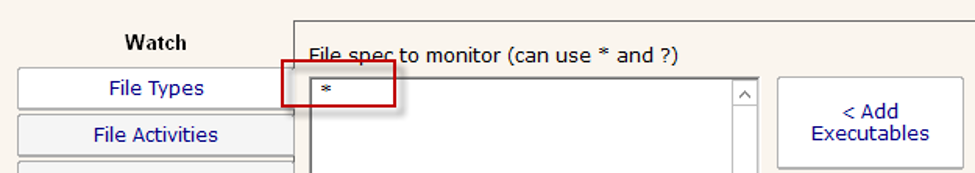
Leave the File Types tab with the default of monitoring all files as shown:
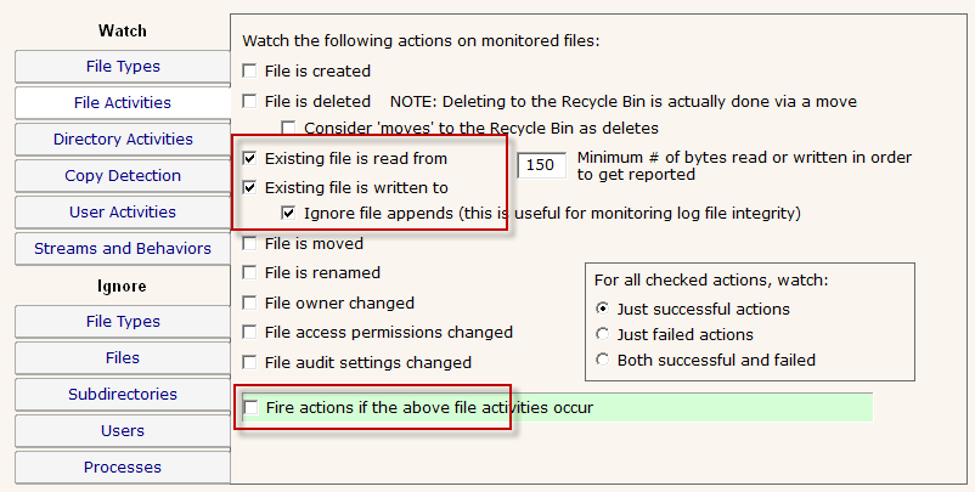
On the File Activities tab, only watch file Reads and Writes as shown below. Be sure to uncheck the green box – we don't want to fire alerts for all file reads and writes.
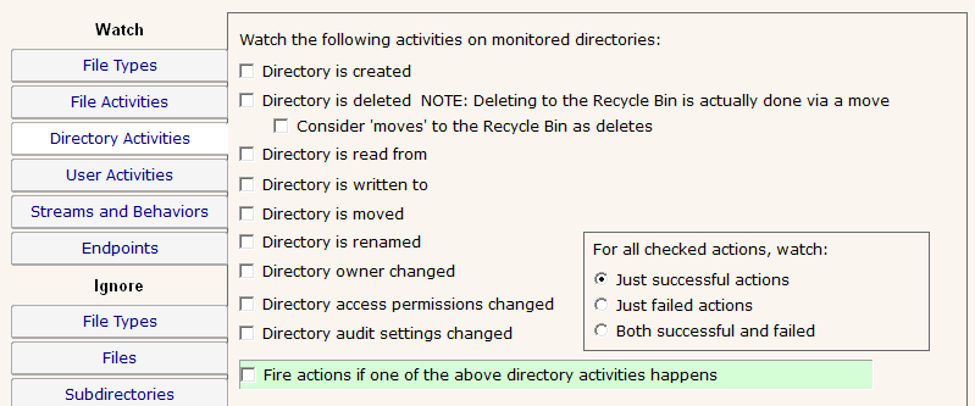
Uncheck all of the boxes on the Directory Activities tab:
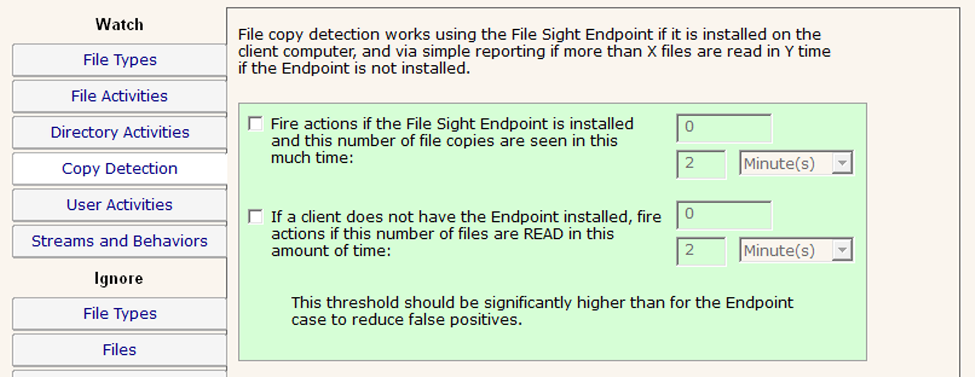
Uncheck all of the boxes on the Copy Detection tab:
In order to be effective, ransomware has to encrypt files. That means it has to:
Some ransomware will write to a different file, and then delete the original file. Some will write into the original file, and possibly rename the file after it has been encrypted. Watching for deletes and renames would help cut down on false positives, but it will also miss any ransomware that doesn't do those final steps.
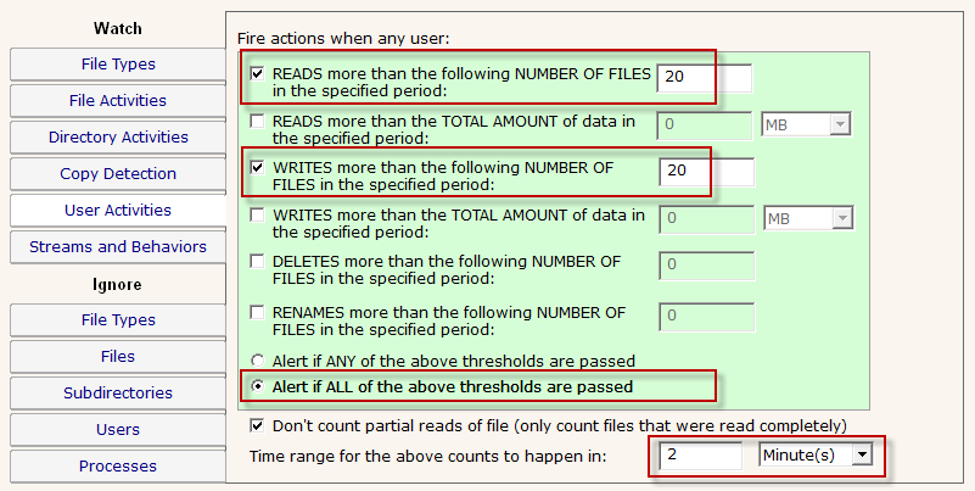
The User Activities tab is the most important. This is where the heuristic thresholds are defined. You want to set it such that a normal user is not impacted. Read AND writing 20 files in 2 minutes is unlikely for a normal user's workflow, and thus a safe threshold.
IMPORTANT: These threshold numbers are suggestions. The action is triggered as soon as the thresholds are passed, not at the end of the time period specified. Increasing the time gives more time for activity to accumulate towards the threshold. Therefore, increasing the time will increase the chance of catching a slow ransomware attack. But it also increases the chance of triggering on a normal user's work flow, so the threshold might need to be higher to prevent false positives.
You can ignore the Streams and Behaviors and Endpoints tabs.
For the Ignore tabs, it's best to ignore anything that might generate 'noise'. For example, a backup application will likely read all the files. There is no reason to record all of that information to the database, so it's best to ignore the backup process. Ignoring the anti-virus application is probably a good idea too. If you don't see those processes listed yet, give it some time and come back to the monitor. PA File Sight will add processes to the list as it sees them.
IMPORTANT: Do NOT ignore the System or Network process. When a user accesses files from across the network, the 'process' they are using will be reported as "System or Network".
If there are particular files you know are changed constantly (maybe things in a spool folder, a logs folder, etc), you could ignore that folder or those files.
Finally, consider if there are user accounts that should be ignored. Normal users should not normally be ignored, but rather any service accounts that might be used for specific operations. For example, if backups are performed by a specific backup account, that account could be ignored.
This monitor is now ready to start detecting ransomware attacks. After the other detection methods are discussed, we'll come back and look at adding actions to add prevention to the detection.
“I keep forgetting how easy you make this software. I love Power Admin. Great product at a very fair price!!”
Erik M., The Milton Bank, USA