Trusted Applications

Making sure that only safe and vetted applications run is one of the best ways to secure servers and end-used computers from many kinds of malware. This feature is sometimes called
application whitelisting, application allow listing or even application locker. We call it Trusted Applications.
With the Trusted Applications feature, you define
rules about which processes can be run, by whom, and
even which files can be read by those applications (to optionally allow scripts to run in very specific situations you might have).
The rules can take into account the following characteristics:
- Path of file/executable being accessed
- Is the path in a local cloud folder (DropBox, OneDrive, Google Drive)
- Path of process accessing the file/executable
- Digital signer or the file and/or process
- Is the path to a cloud drive or external drive
- User account making the request
- User's group membership
- Is file, user or digital signer in various lists
- The requesting hostname
- Is the Endpoint running on the requesting computer
- ... and more. See the list of statements
The rules are easy to write because they can refer to various lists of files, folders,
product companies (application signers), users, etc. Just a few rules can quickly create a large amount of
safety for many systems.
Handling the exceptional cases is easy too (example: it's simple to add the one-off application that needs to run in the Finance department).
Trusted Applications rules can be used on servers, as well as client computers via the optional Endpoint.
Access Control Based on Heuristics and Behavior
You could create rules like the following examples:
- Prevent browser processes from loading Word or Excel documents (to prevent them from being uploaded or emailed)
- Prevent Word documents from being read by anything other than Word.exe (to help prevent copying)
- Alert if files in a certain honeypot folder are accessed
- Don't allow unknown programs to start
- Don't allow browsers to write to .exe files (i.e. not allowed to download and save an executable file to disk)
- Prevent clients that are not running the Endpoint (since they might not be as safe) to access files on a server
See some default rules below to see how easy they are to define:
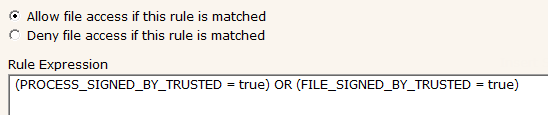
- Allow trusted files and apps from trusted companies
- (PROCESS_SIGNED_BY_TRUSTED = True) OR (FILE_SIGNED_BY_TRUSTED = True)
- Apps from Trusted Application list can run
- PROCESS_IS_TRUSTED_APP = True
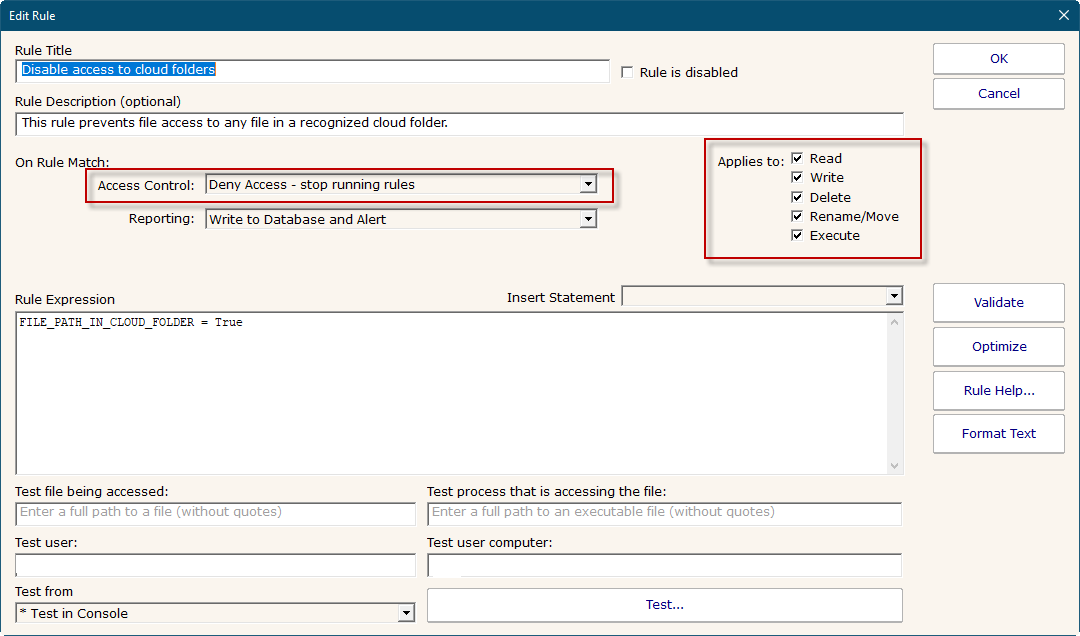
- Disable access to cloud folders (deny rule)
- FILE_PATH_IN_CLOUD_FOLDER = True
- Full Access Users can access anything
- USER_IS_FULL_ACCESS = True
- Only allow Powershell scripts from the Windows folder
- (FILE_PATH != "%WINDIR%*") AND (FILE_IS_TEXT_FILE = True) AND (PROCESS_PATH = "*Powershell.exe")
- Prevent Command Host files, unless an Administrator or Trusted Application
- (FILE_IS_COMMAND_HOST = True) AND NOT ((PROCESS_IS_TRUSTED_APP = True) OR ((USER_GROUPS = "*,Administrators,*") OR (USER_GROUPS = "*,Domain Administrators,*")))
- Stop trusted app from launching or reading a non-trusted app (deny rule)
- (((PROCESS_IS_TRUSTED_APP = True) OR (PROCESS_SIGNED_BY_TRUSTED = True)) AND (PROCESS_IS_COMMAND_HOST = False)) AND ((FILE_IS_EXECUTABLE = True) AND (FILE_SIGNED_BY_TRUSTED = False))
Block Users From Uploading Files to OneDrive, Google Drive or DropBox
The FILE_PATH_IN_CLOUD_FOLDER statement makes it very easy to block files from being written to cloud drives, and it can even prevent files from being read from a cloud drive.