- Solutions
-
- File Server: Ransomware Protection
- File Server: File Copy
- File Server: Audit File Access
- File Server: Storage growth reporting
- Licensing/Pricing
- Contact
This help page is for version 9.1. The latest available help is for version 9.4.
The File Sight monitor watches file and directory I/O take place and can record and alert you on many different conditions. When configuring the monitor, the first thing to decide is where to monitor. Generally there will be a directory that you're interested in. It is more efficient to monitor just that directory rather than an entire drive. You can create multiple File Sight monitors to watch various drives / directories in a computer.
In the dialog below you'll see there are many options. After specifying the root directory to monitor you can specify whether all subdirectories should also be monitored. Database recording is only available in the Ultra product version -- it is not available in the Lite edition.
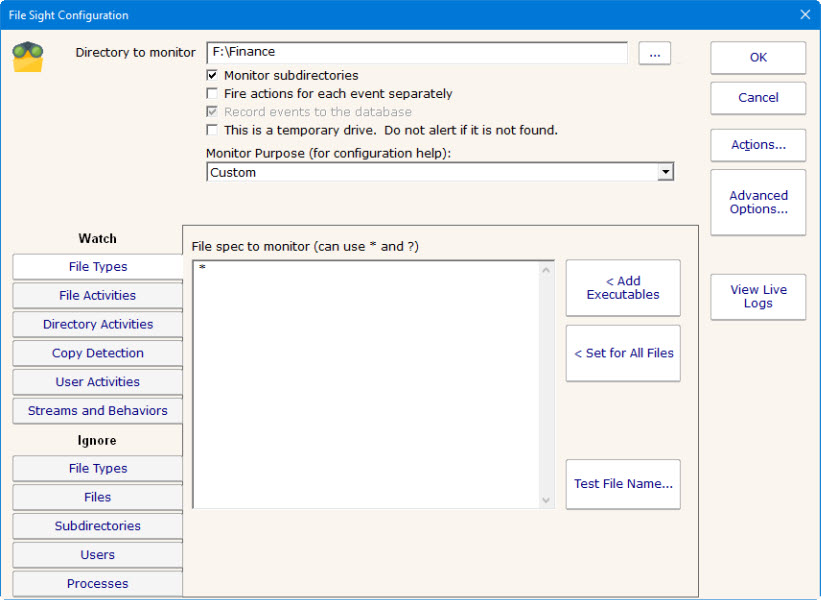
This monitor has standard buttons on the right for Adding Actions and setting Advanced Options.
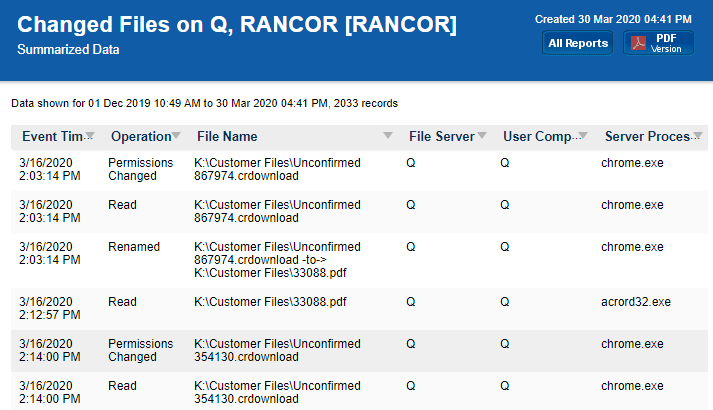
A variety of reports are available for PA File Sight, including:
All ChangesThe Ultra version of PA File Sight supports reports which can tell you about file and directory activities that have taken place in the past while PA File Sight was monitoring the server. You can report on changes to particular files or directories, changes made by a particular user, types of changes (all deletes for example), and any of this during a specific time frame.
Having issues with File Sight? Take a look at the troubleshooting guide.
Reports and alerts can contain even more information if the client Windows computer that accesses files on the server is running the File Sight Endpoint.
This check box indicates whether just the target folder should be monitored, or all child folders as well.
By default everything that a monitor sees on a single scan will all be reported together. You can have each individual reportable event (each file Delete, Write, etc) reported on separately. This is useful when sending File Sight alerts to a SIEM or other 3rd party application.
This is checked for Ultra installations, and unchecked for Lite installations.
Normally if a drive can't be found an alert will be fired. If the drive is removable, or part of a cluster that might not be available sometimes, this setting will prevent the 'drive not found' type of alerts.
The Monitor Purpose allows the monitor to audit its own settings and give configuration hints to ensure the monitor can meet the stated purpose. For example, if you want to be alerted about file copying but don't have any alerts attached, this monitor will highlight that using a red banner. Set to Custom to disable all configuration hints.
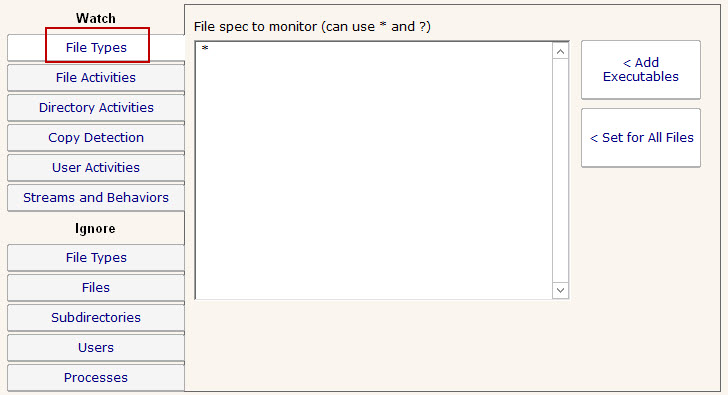
File Types tab lets you specify which files to consider. You can use typical * and ? wild card in specifying file types. Don't include paths here -- this is just for file types (for example *.doc would consider only file I/O that was on *.doc files).
The File Activities tab is where you specify exactly what types of file I/O that you're interested in. File reads, writes, creates, deletes and moves can all be filtered on. For reads or writes you can further filter out very small reads which might happen if Windows Explorer displays a directory.
The green box on the File Activities panel specifies whether actions should be fired when a matching file I/O activity happens. Sometimes this is unchecked because actions/alerts aren't needed, but the matching activities can still be written to the database.
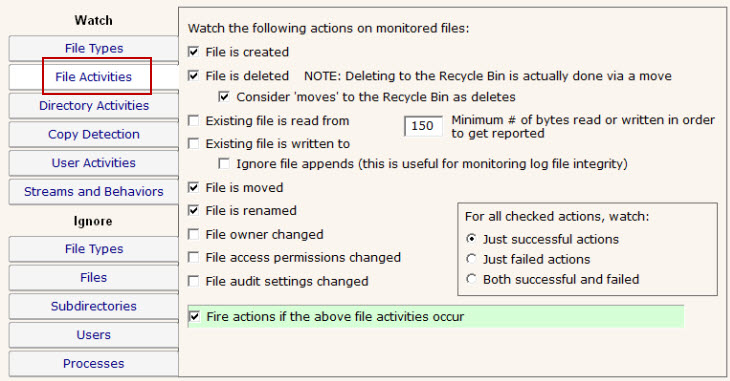
NOTE: Only the Ultra version of the product supports a database and reporting, so the "Fire actions if the above file activities occur" check box is almost always checked for a Lite installation that only does alerting.
If you are interested in specifically directory actions, the Directory Activities tab is where you can specify them. This panel works just like the File Activities panel did, except it is focused on directories instead of files.
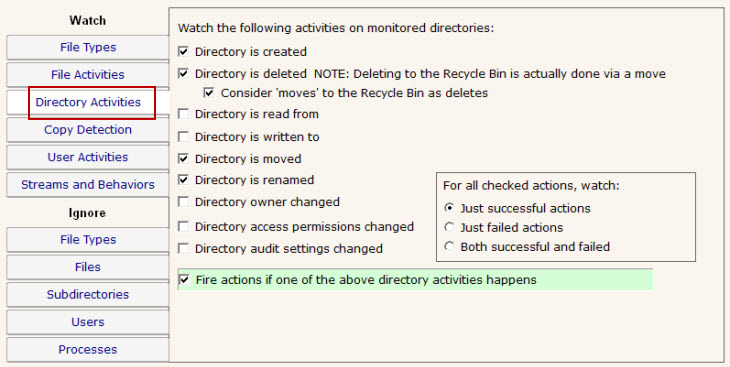
NOTE: Only the Ultra version of the product supports a database and reporting, so the "Fire actions if one of the above directory activities happens" check box is almost always checked for a Lite installation that only does alerting.
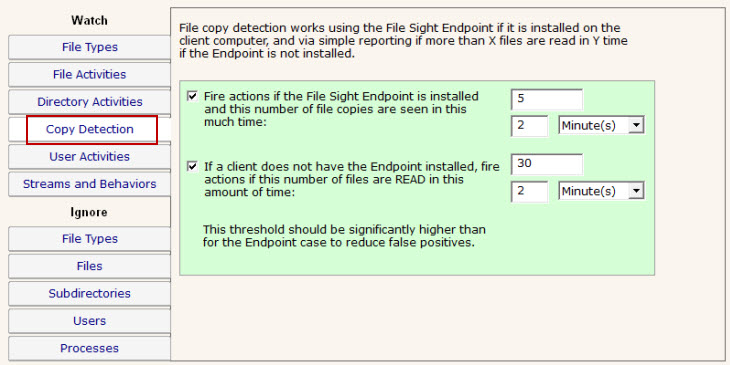
NOTE: Only the Ultra version of the product supports Endpoints.
File Sight Endpoints allow directly detecting when file copying happens. You can choose to receive alerts when a file copy operation is detected by an Endpoint by checking the box and indicating how many copies have to be seen. If there are clients that are not running the Endpoint, you can indicate you want to be alerted after they read X number of files in some amount of time. Note that reads don't necessarily indicate copies, but without the Endpoint, the server has no way of knowing where the read file ends up.
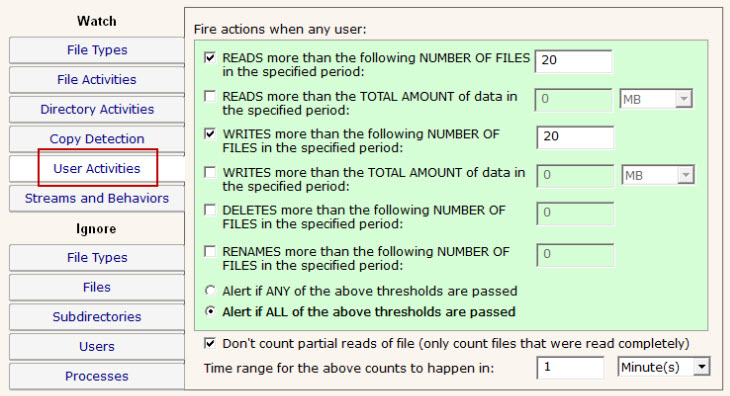
NOTE: This panel is only available in the Ultra version of the product.
The User Activities panel is very powerful. It lets you specify alert conditions which are based on the number or amount of files that a user interacts with. These settings are all in a green box, which means they run actions (alerts) when the thresholds are met. These settings do not however cause anything to be written to the database. Be sure and set the corresponding settings in the File Activities panel if you'll want to run reports later and find out what was read or written to.
When one of the conditions is met, the fired alerts will list the files that caused the condition to be triggered.
In addition, for file reads you can check the box indicating you only want to count complete file reads. Some administrators use this to try and detect a user copying a directory of files. At the file system level where this monitoring is taking place, it is impossible to detect where a file ends up once it is read (it could go straight to memory, to paper via a printer, out via an email, or copied to a different location on a disk). However, if many files are read completely in a very short time, that matches the heuristics of a file copy process.
This panel lets you specify how to handle file streams that encountered, as well as
whether File Sight should try and interpret typical application behaviors.
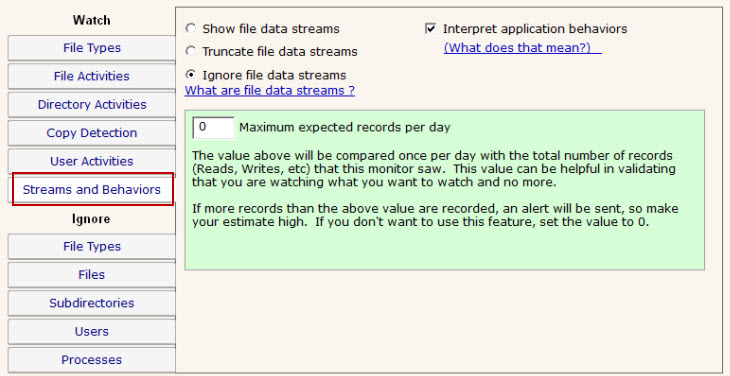
The "Maximum expected records per day" option is really just to help you verify that you are collecting roughly the number of file activity records that you expect to be recording.
Similar to the Watch: File Types tab above, this tab lets you specify files using wild cards. In this case however, files that are seen that match the specification are ignored and not alerted on nor written to the database.
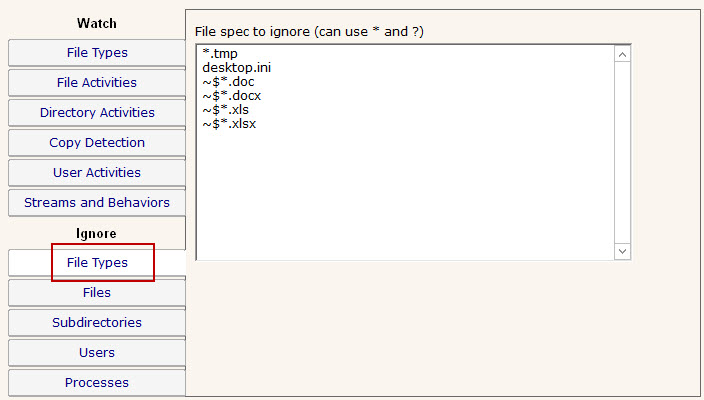
The Ignore: Files panel lets you specifically ignore files, perhaps because they are just work files, temp files or otherwise unimportant. In this dialog you specify the file using the full path to the file.
If you enable Training via the Advanced Monitor Options, the monitor will watch all matching file I/O and automatically add all ignored files that are accessed during the training period to this list.
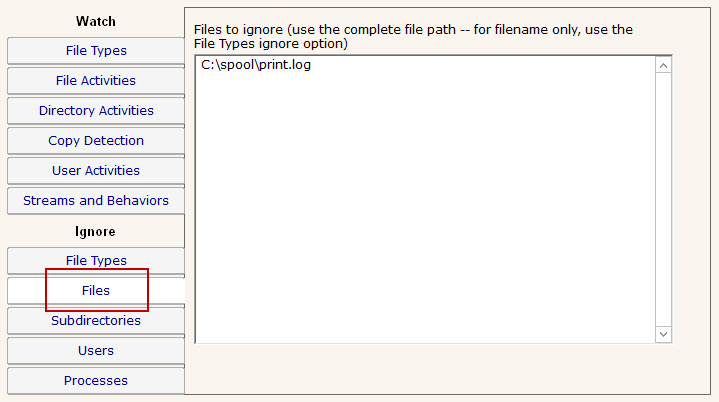
If you need to ignore specific directories below the main directory that you're watching (perhaps a temp directory or a queue directory), you can specify the directory to ignore here. In this case wild cards do not work, but sub-path matching does. That means you can specify the entire directory path to ignore, or you can ignore just a part.
For example, if you enter \TEMP, that would match on C:\TEMP\, C:\TEMPORARY and C:\DOCS\TEMP\ because the characters "\TEMP" were found in each of those paths. If you didn't want to match on C:\TEMPORARY for example, you could filter on "\TEMP\".
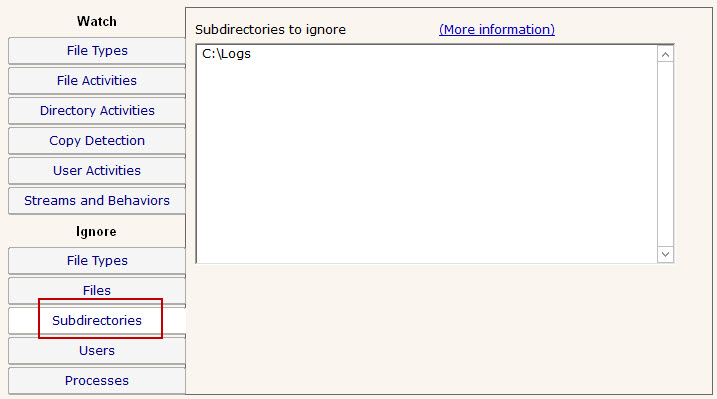
Often there are particular user accounts, particularly accounts that do automated processing like virus scanning, that should not be logged (if for no other reason than to keep the reports easier to review). You can select those user accounts to ignore on this tab.
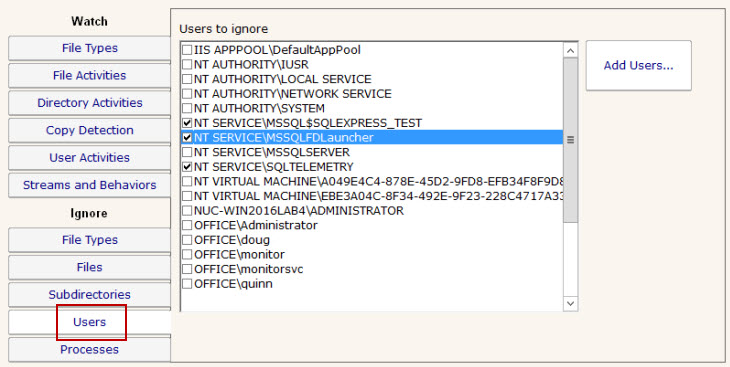
Similar to the Ignore: Users tab above, there are often reasons to ignore specific processes (perhaps that do automated processing of files) from alerting and being written to the database. These processes can be specified here. Note that only processes that have already been seen are listed.
When a file or directory access takes place that meets the filter criteria described above, PA File Sight can alert on that event. By default, it uses the following format:
Op: CreatedThis format is configurable via the FS_LineFormat registry value.
The Op line (short for Operation) can be one of the following list of values:| Operation | Notes |
|---|---|
| Created | A new file that didn't exist before exists now |
| Deleted | The file was deleted. Note: The Save routine for some applications (Microsoft Office for example) happens by saving to a temporary file, deleting the original file, and then renaming the temporary to the original file name. File Sight sees this and properly reports the file deletion. If you don't want this behavior, see the Interpret Application Behavior option. |
| Read | Some or all of an existing file was read from disk. Note that clicking a file in Explorer often causes a part of the file to be read (author information, icon is extracted, etc). In addition, clicking a file might cause an anti-virus app to scan the file. PA File Sigth sees and can report on all of this. To avoid some Read reports, you can indicate that at least 200 bytes of the file must be read (that would filter out icon extraction by Explorer). |
| Renamed | A files was renamed, or moved to the same drive (the operating system calls moves 'renames') |
| Wrote | An existing file was written to (ie changed) |
| Audit Changed | Audit settings on the file were changed |
| Permissions Changed | File access permissions on the file were changed |
| Owner Changed | The file's owner was changed |
| Group Changed | This is not usually seen, but is listed in this table for completeness' sake |
| Failed to Create | |
| Failed to Delete | |
| Failed to Read | |
| Failed to Rename | |
| Failed to Write | |
| Failed to Change Audit | |
| Failed to Change Permissions | |
| Failed to Change Owner | |
| Failed to Change Group |
The values above can be translated into a local language.