Category: How To
-

How to Prepare Your Staff for Hybrid Cloud
By Des Nnochiri Budgetary constraints are often a key factor in determining how an organization sets up its IT infrastructure. The hybrid cloud typically leads to cost savings of between 5% and 30% for enterprises that make the transition. Besides the monetary aspects, performance benefits and easier administration also inspire many organizations to consider […]
-

How to Move on from Windows 7
Despite the appearance of new and supposedly improved versions of its operating system, Microsoft’s Windows 7 is proving to be a tenacious and popular environment, both for individual and corporate users. 2019 estimates suggest a third of Windows consumers are still clinging to version 7. Nevertheless, the company has signaled its intentions to withhold […]
-
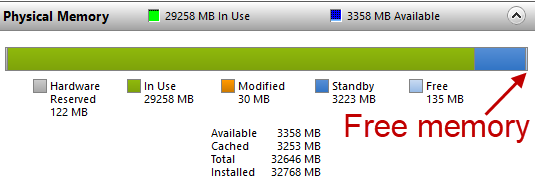
Computing Memory Usage According to Task Manager
When you look at Task Manager, it’s hard to compare it to any counter you see in Performance Monitor. The reason is there are many ways to discuss memory usage and it’s cousin free memory. If you think about it, you really don’t want your computer to have free memory laying around. That would represent […]
-
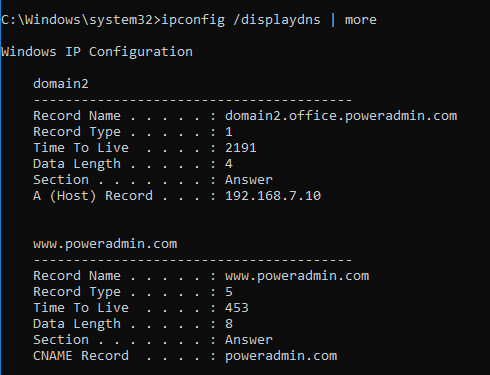
Ping and the Windows DNS Cache
We’ve been chasing an issue lately and learned a few things, so we thought we’d document them for posterity. When you use the Windows ping command line utility, you give it an IP address or host name, it resolves the host name if needed, pings the address, and gives you the results. Simple, right? […]
-

Windows 10 Optimization Tips: Stability & Downsizing
By Des Nnochiri In the first installment of this two-part guide, we considered various ways of improving the performance of Windows 10. To conclude, we’ll be looking at methods for downsizing your Windows 10 installation to promote stability and increase your levels of security and privacy. Disabling Notifications The Windows 10 Action […]
-
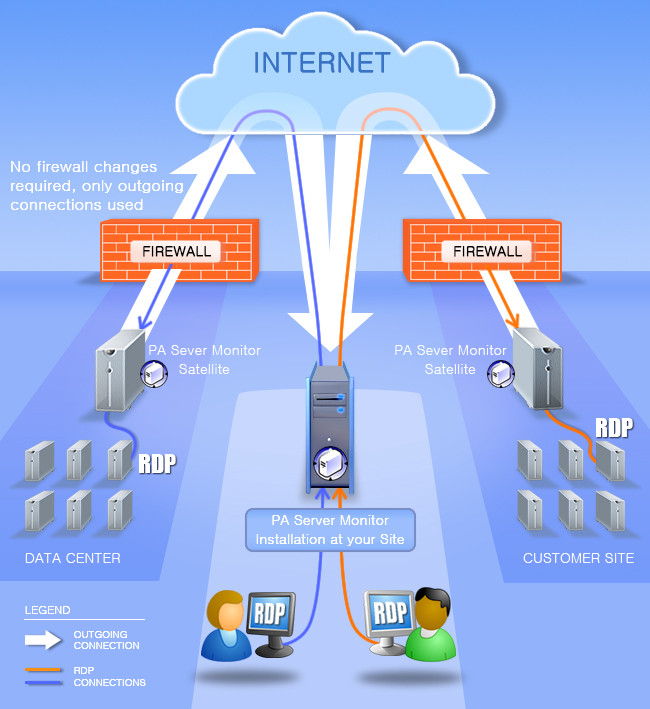
Almost Free Remote Support / Remote Access Tool
Executive Summary: Practically unlimited remote desktop support / remote access for a one time cost of $125! Just install the remote agent and you can access devices at the remote agent’s site. It just works! Really? Sounds like a scam? No, we’ve had this underappreciated feature for years. Time to get the word out […]



