By Des Nnochiri
The Windows 10 operating system has had a reputation for poor design and lax practices on information privacy and security for some time. It’s debatable exactly how bad the OS actually is or isn’t in this regard. In this article, we’ll be exploring some methodologies and best practices for hardening the security status![]() of your Windows 10 workstations and network configuration.
of your Windows 10 workstations and network configuration.
Disable Server Message Block (SMB) Version 1
Server Message Block (SMB) is an internet standard protocol which has been used on top of the TCP/IP protocol for many years by Windows systems. SMB enables Windows 10 to share files, printers, and serial ports. Version 1 of the protocol (SMB v1) has been around since Windows 95 and remains in use to this day. As you might expect, within that time, several exploits and abuses of SMB have been developed. Blended attacks combining ransomware with other strains of malware are most common—and any Windows 10 network still deploying this early version of the standard is very much at risk.
If you’re familiar with editing the Windows 10 registry, then group policy with a registry key may be used to disable SMB v1 on any hardware that’s running it. Alternatively, you may follow the guidelines in Microsoft’s KB2696547 security update to detect if SMB v1 is present on a system and use the specified procedure to disable it.
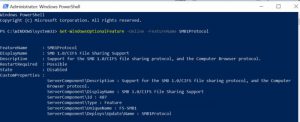
Windows 10 allows you to use PowerShell to determine if SMB v1 has been enabled. PowerShell will return the currently-enabled SMB state of a machine when you type the following syntax:
command Get-WindowsOptionalFeature –Online –FeatureName SMB1Protocol
(Image Source: CSO Online![]() )
)
SMB v1 can also be blocked at the firewall and internet levels of your network. Most firewalls will do this by default, blocking all versions of SMB at the network boundary via TCP port 445 with related protocols on UDP ports 137-138 and TCP port 139.
Copiers, printers, and network-accessible storage devices on older systems may still rely on SMB v1 for their functionality. Having assessed the potential risk of allowing these devices to continue using the protocol, you may need to contact the vendors to find out if there’s a firmware upgrade available that supports a more recent version of SMB.
Later versions of the Server Message Block protocol offer greater protection, particularly in the strength of data encryption and user authentication that they provide. If you must use SMB on your Windows 10 network, then be sure to upgrade any existing installations to SMB version 3.0 or above.
Adjust Your Firewall and Proxy Settings
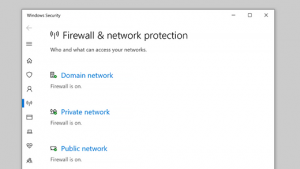
As with any computer network, certain pieces of hardware and software may be the standard for maintaining security. Antivirus or anti-malware suites, intrusion detection/prevention mechanisms, and system-monitoring devices would be examples. Firewalls would also come into this category, and unless your network employs independent or third-party firewall protection, your Windows 10 security regime will need to take the proper configuration of the operating system’s native firewall into account.
(Image Source: Microsoft![]() )
)
The Windows 10 firewall now supports Windows Subsystem for Linux processes. So if you’re hosting Linux in virtual machines, you can add exceptions in the firewall for Linux processes such as SSH or web servers like Nginx.
Adjust Your Privacy Settings
As previously suggested, Windows 10 has been accused of serving as a data harvesting tool, giving Microsoft and its affiliates access to names, contact data, demographics, location, usage statistics, payment credentials, and other sensitive information. And the first stage in configuring Windows 10 for privacy is to go through the privacy policy and terms of service associated with the OS.
Armed with this knowledge, you can then use Start > Settings > Privacy to access the Privacy settings area of Windows 10. Options available generally allow you to either turn a feature on or off, or to leave it on – and then specify which apps or processes it should apply to.
(Image Source: Heimdal Security![]() )
)
In particular, you should pay attention to the following:
- Location: Turn location tracking on only for those features or services that actually require it.
- Account Info: Enable two-factor authentication for your Microsoft account, and don’t store credit card information.
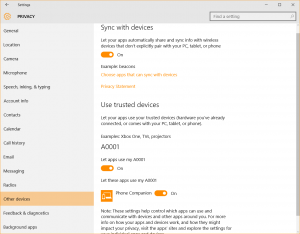
- Call history: Together with Contacts and Messaging, this is the kind of information which should be guarded jealously from unauthorized third parties.
- Other devices: Use this option to regulate how your network devices can connect to one another and share data.
(Image Source: Heimdal Security![]() )
)
Configure Dedicated Workstations or Virtual Machines for Windows 10
Dedicated workstations and virtual machines on your network should be configured to access sensitive premises or cloud assets—preferably via a robust privileged access or identity management solution/service.
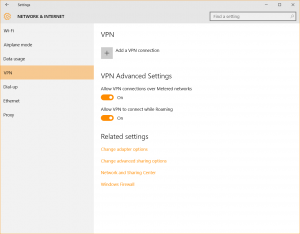
Adjust Your VPN Settings
Virtual Private Network (VPN) services and local software configurations may be accessed in Windows 10 via Start > Settings > Network & Internet > VPN.
(Image Source: Heimdal Security![]() )
)
Note that Windows 10 doesn’t offer a VPN solution of its own, so the settings you specify will be those of your chosen third-party VPN product or service. Ad-blocking and the anonymization of your internet connections (as provided by your VPN) may be supplemented by external tools for malware protection and online security.
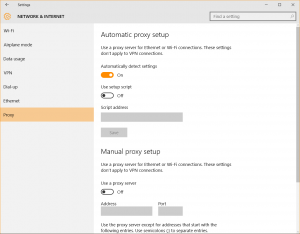
Start > Settings > Network & Internet > Proxy will give you access to the Windows 10 proxy settings, where you can either use a setup script, or do a manual proxy setup to gain an additional layer of security and privacy.
(Image Source: Heimdal Security![]() )
)
Exercise Due Diligence with Updates
In addition to privacy concerns![]() , the technology press has also voiced its fair share of alarm over the patchy nature of Windows 10 update cycles and the unfortunate effects that improperly tested upgrades have had on user systems.
, the technology press has also voiced its fair share of alarm over the patchy nature of Windows 10 update cycles and the unfortunate effects that improperly tested upgrades have had on user systems.
For this reason, it’s a good idea to have at least one “sheep dip” workstation (isolated from the rest of the network), for testing the effects of the latest updates and security patches. You may also contact your vendors—particularly suppliers of third-party security products—for their take on how the latest upgrade affects any dependencies their software or hardware might have. Success on this machine may then give the green light for more general updates across the network.
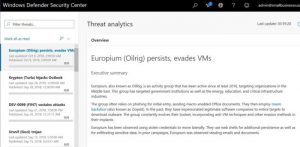
Get Up-to-Date Threat Intelligence
(Image Source: Heimdal Security![]() )
)
In Windows 10, the Defender Security Center Threat Analytics dashboard is available to any organization running Windows Enterprise E5, or having a Microsoft 365 E5 subscription. The dashboard lists recent cyber-attacks and security risks, and posts updated information about recent threats and security incidents that specifically targeted the Windows operating system. It also gives advice on mitigating and defending against such attacks.
(Image Source: Heimdal Security![]() )
)
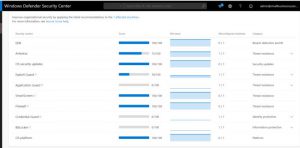
For organizations that don’t run Enterprise E5 or subscribe to Microsoft 365 E5, the Windows Security Center and Windows Time service feature a security providers section which gives insight into all the antivirus, firewall, and web protection software that’s running on your system. For Windows 10 network security, Windows Defender Antivirus will remain enabled in conjunction with any of your security software that hasn’t been registered as a protected process.