Category: How To
-
PA Server Monitor Basics & Getting Started Guide
PA Server Monitor is our flagship product that was designed with the end-user in mind. It is the easiest server monitoring solution to install and use. Once installed, our PA Server Monitor is designed to provide agentless server monitoring to track and monitor various server aspects, including: CPU Usage Memory Usage SNMP, Traps, and Syslog […]
-

A Checklist for Your Website Launch
Launching your business website is a big step, but, if you don’t know how to launch a website the right way, you’re just wasting time. There are many considerations, including design, functionality, SEO, testing, marketing, analytics, and security. Assuming you’ve designed and built a site that’s ready to go, your website launch checklist should include […]
-
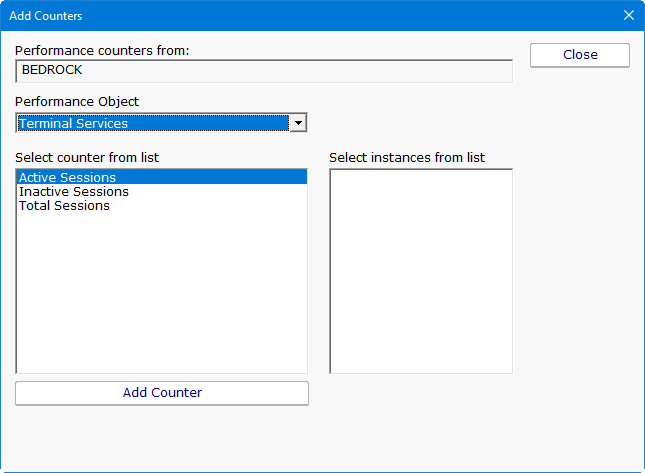
Monitoring Remote Desktop (RDP) Performance
With so many people working from home now, Terminal Servers and Remote Desktop Gateways are surely getting exercised like never before. Perhaps you want to monitor them to see how busy they are, and alert if there are problems. Below are a few ideas. CPU of Course Naturally you need to monitor the server’s CPU […]
-
Great Monitoring Article
We frequently get people asking us for some best practice advice. Today I came across a Google article that is well written and gives some great advice on setting up monitoring. It’s available at: https://landing.google.com/sre/sre-book/chapters/monitoring-distributed-systems/
-
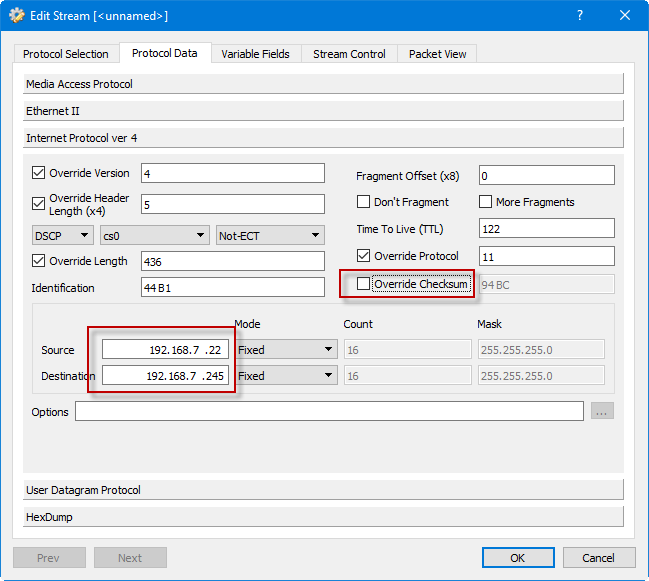
Replaying and Redirecting a Network Capture from a Different Network
Recently we had a case where the SNMP Trap Monitor was truncating text from the received trap. The customer captured some example SNMP Trap packets using Wireshark, and then sent us the capture file. Wireshark is an awesome application to look at network traffic and we highly recommend it. But back to the network […]
-
Implementing 3rd Party Fail Over with the Service Monitor
We have a customer with a scenario where a set of services run on SERVER1 -or- SERVER2. If any service in a set fails, everything in the set should be stopped and the entire set should be started on the other server. Below I’ll describe how to implement this. In my example I’ll assume […]
-

How to Keep Malware Out of Your Printers
The landscape of cybersecurity is always changing, and new threats are constantly emerging. One of the newest – and the most interesting, if you are into that kind of thing – is the rise of printer malware. This type of malware started to be reported in November 2017, when Barracuda Labs saw an attack […]
-

How to Print and Scan Documents with Android
Mobile apps for Android are so numerous and varied that it’s possible these days to do most of the work of a conventional office from a single handheld device. However, handhelds can’t do everything (yet),.and the limitations of a small screen can make it preferable to share or print documents to a larger format. There […]
-

How to Manage Linux Logs
By Des Nnochiri Log files in Linux often contain information that can assist in tracking down the cause of issues hampering system or network performance. If you have multiple servers or levels of IT architecture, the number of logs you generate can soon become overwhelming. In this article, we’ll be looking at some ways […]
-

How to Monitor Hybrid and Multi-Cloud Networks
By Des Nnochiri Most enterprises now use two or more cloud service providers, and 35% use up to five monitoring tools to keep tabs on hybrid cloud and multi-cloud environments. Even before organizations began shifting software and IT infrastructure to the cloud, a typical business would use four to ten tools just to monitor […]