-

5 Things Only Experts Know About Server Monitoring
Server monitoring is a valuable tool when it is set up and configured correctly. With a server monitoring service, there are several things you can do if you have the right knowledge. Obtaining that knowledge is easy when you have experts in your employee or on contract. For others, access to experts is not […]
-

5 Remote Working Best Practices and Tips in the Era of Coronavirus Pandemics
As the COVID-19 pandemic sweeps the world, the need has arisen for workers everywhere to adopt remote working practices wherever possible. Remote working presents many opportunities for both businesses and individuals to make better use of their time and enjoy a more streamlined approach to task delegation. Through the use of specialized software, such […]
-

Use Active Directory Monitoring to Protect Remote Active Directory Logins
Active Directory (AD) is a process service that is used in Microsoft® Windows-based environments. It is responsible for authenticating users when they connect to servers and for authorizing access to different directories, files, and data. AD is also responsible for carrying out security protocols on all connected devices and computers. For example, there is […]
-
Benefits of Active Directory and Network Performance Monitoring
With more people working from home due to the coronavirus, businesses of all sizes need to have remote policies in place that help protect their data, ensure employees are working, and see that security practices are being followed. There are several methods to do these things that do not cost a fortune. For instance, you […]
-

Help Your IT Staff Identify Security Breaches with a Cybersecurity Training Plan
In today’s digital age, having secure data solutions is essential for improving data loss prevention. Part of this solution should also include a cybersecurity training plan for your IT staff. Many companies make the mistake of pricing the tools to help prevent data breaches but never take the time to ensure their employees are properly […]
-

What Are the Pros and Cons of File Sharing?
File sharing is a method used by some organizations where multiple employees have access to the same files. How the files are accessed does vary depending on the user environment. The files could be shared between two computers, where the files are stored on one computer and another user accesses them from their workstation. […]
-

PA Server Monitor Basics & Getting Started Guide
PA Server Monitor is our flagship product that was designed with the end-user in mind. It is the easiest server monitoring solution to install and use. Once installed, our PA Server Monitor is designed to provide agentless server monitoring to track and monitor various server aspects, including: CPU Usage Memory Usage SNMP, Traps, and Syslog […]
-
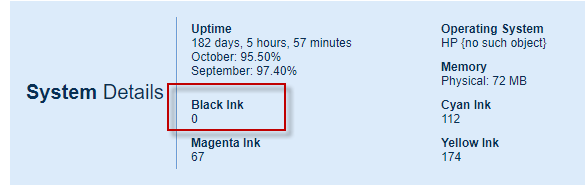
Custom SNMP Inventory / System Details values
Did you know you can add custom values to the System Details panel that are looked up from a device via SNMP? It’s pretty easy – let me show you how. First, look at C:\Program Files\PA Server Monitor\InventoryList.txt It is a simple file that allows you to specify a title, a type (string […]
-

How to Leverage File Monitoring as an Effective Breach Detection Tool
One thing that all organizations of any size need to realize is that data breaches only occur when there are not sufficient breach detection tools in place. Simply having a data loss prevention system does nothing unless you are actively using it to identify and stop a data breach from occurring. This is not […]
-
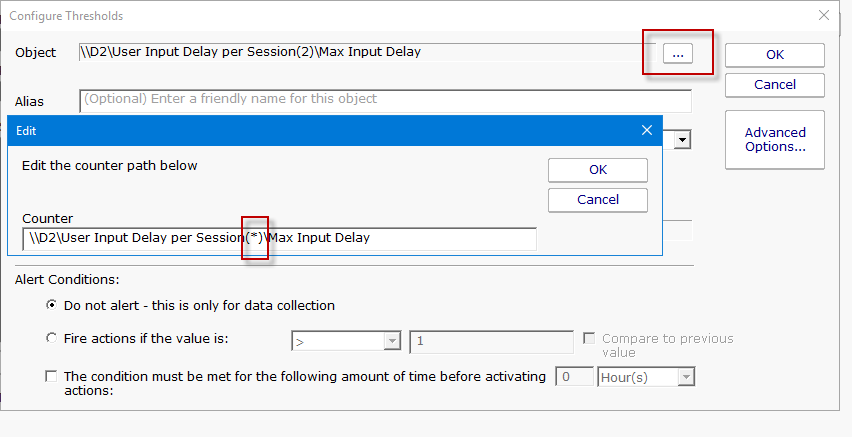
Diagnosing Remote Desktop Application Performance Problems
With so much Work From Home (WFM) going on these days, system administrators likely have many people using Remote Desktop, hopefully through Remote Desktop Gateway, to access their work computers to accomplish their work. Usually Remote Desktop works great – it’s been tuned well and offers good performance. Sometimes it doesn’t and that’s when […]
Got any book recommendations?