-

Data Breach Detection Measures Include Using a Data Loss Prevention System
The network security basics for your organization should include some type of data breach detection tools. Data breaches are on the rise in recent years, including stealing personal information about employees and customers. From credit card numbers to social security numbers and pay records, hackers have stolen a wide range of data from businesses of […]
-

Email Security Risks: Why You Need a Cyber Security Plan
Even though technology has advanced significantly over the past few decades, hackers and cybercriminals still target large volumes of email messages daily. Some of the biggest types of things that get sent through email include malware, ransomware, trojans, and viruses. These things are often disguised in some sort of “friendly” email message, an embedded […]
-

How to Prevent, Detect, and Remove Spyware
Spyware is a type of malware that hides deep inside your computer. Unlike more visible types of malware, spyware lets you go about your tasks while secretly recording information—especially passwords and other sensitive credentials. Since spyware is difficult to notice, both home users and system administrators need to prioritize its prevention and detection. Thankfully, […]
-

How to Implement a Strong COVID-19 Cybersecurity Plan
As COVID-19 forces more employees to work from home, companies are reevaluating their cybersecurity plans to place an increased emphasis on securing remote access, as well as phishing and ransomware prevention. Here are some of the most important security basics to include in your COVID-19 cybersecurity plan. Secure Remote Access Employees working […]
-
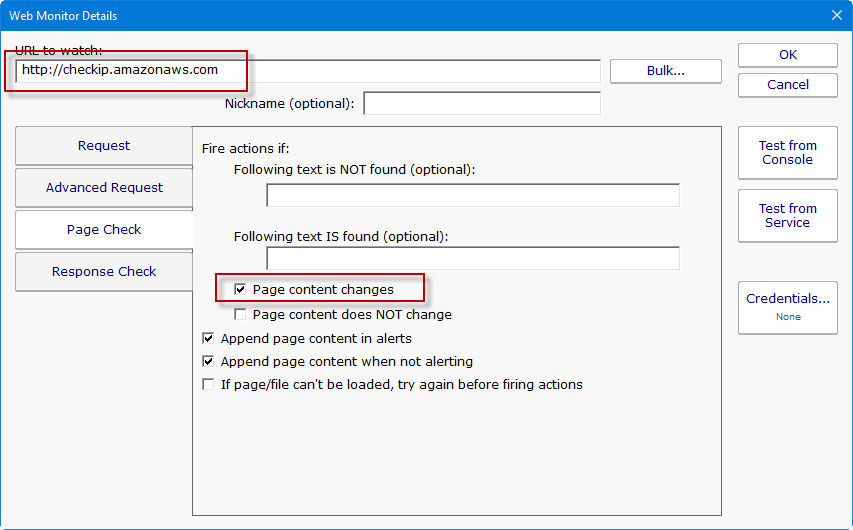
Get Alerted When Your External IP Address Changes
We have the most clever customers 🙂 One customer setup a Web Page monitor to watch http://checkip.amazonaws.com which simply returns your current external IP address. The monitor can alert if the returned data changes so that makes it super easy to find out if you address changes. You could even have it run […]
-

Introduction to Database Security: Security Basics You Need to Know
Database security is essential to keep your business’s data and files security from others that do not need access. Whether you are a small business owner or are a database administrator for a medium or large company, you need to have a solid understanding of data security basics. Why Is Database Security Necessary? Database security […]
-

How to Determine What Data Privacy Security Controls Your Business Needs
Data breaches and ransomware are two of the biggest concerns businesses have about data security management and control. Data security is implementing the right procedures to protect your data, files, and user information on your network whether it is running locally or in the cloud. When deciding what types of data privacy security controls your […]
-

The Top 6 Benefits of Web Hosting for Your Business
Website hosting is growing in popularity with businesses of all sizes. Instead of having to maintain your in-house web server, you pay a monthly subscription to someone else to host the website for you on their server. There are several benefits of web hosting for your business when using a hosting provider. 1. No In-House […]
-

Ransomware: 11 Steps You Should Take to Protect Against Disaster
The frequency and volume of ransomware attacks have increased dramatically in the past few years. Few people in the tech industry will forget the 2017 WannaCry attack, which infected over 200,000 computers in 150 countries worldwide and brought down part of the U.K.’s National Health Service, or the 2019 RobbinHood attack, which brought the Baltimore […]
-

Product Directory Rights
We are frequently asked about which rights are needed in the product directories. PA Server Monitor, PA Storage Monitor and PA File Sight share a common directory layout. In general, the monitoring service account will need full read access to the product’s root directory. That would be: C:\Program Files\PA Server Monitor C:\Program Files\PA […]
Got any book recommendations?