Category: How To
-

How to Configure PA Server Monitor to Monitor Your Event Logs
Did you know that you could configure PA Server Monitor’s Event Log Monitor feature to monitor one or more of your event logs? The event logs can include standard application, security, and system logs, as well as any custom event logs you want to monitor. With our server monitoring software, you have complete control and […]
-

Steps for Developing IT Organization Strategies for Your Business
Does your IT department perform re-actively to problems as they occur or are they proactive, attempting to head off problems before they occur? Sadly, many IT departments are reactive because they lack the proper IT organization strategies to use technology and apps to become proactive. Taking a reactive approach is ineffective and affects productivity […]
-

5 Remote Working Best Practices and Tips in the Era of Coronavirus Pandemics
As the COVID-19 pandemic sweeps the world, the need has arisen for workers everywhere to adopt remote working practices wherever possible. Remote working presents many opportunities for both businesses and individuals to make better use of their time and enjoy a more streamlined approach to task delegation. Through the use of specialized software, such […]
-

Help Your IT Staff Identify Security Breaches with a Cybersecurity Training Plan
In today’s digital age, having secure data solutions is essential for improving data loss prevention. Part of this solution should also include a cybersecurity training plan for your IT staff. Many companies make the mistake of pricing the tools to help prevent data breaches but never take the time to ensure their employees are properly […]
-

How to Leverage File Monitoring as an Effective Breach Detection Tool
One thing that all organizations of any size need to realize is that data breaches only occur when there are not sufficient breach detection tools in place. Simply having a data loss prevention system does nothing unless you are actively using it to identify and stop a data breach from occurring. This is not […]
-
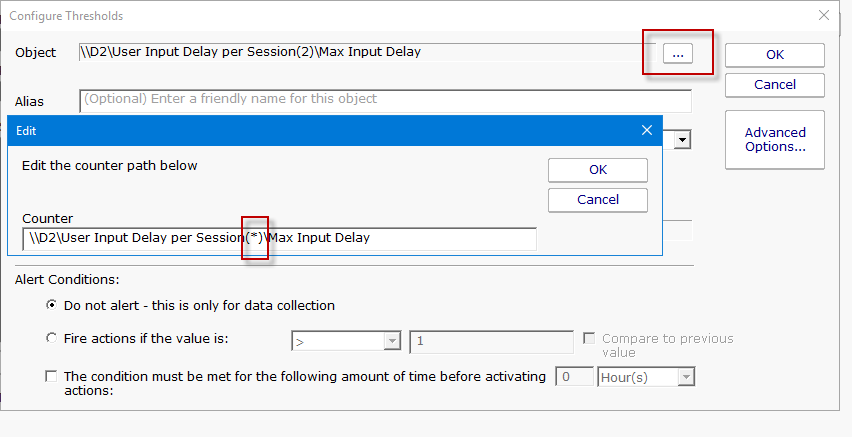
Diagnosing Remote Desktop Application Performance Problems
With so much Work From Home (WFM) going on these days, system administrators likely have many people using Remote Desktop, hopefully through Remote Desktop Gateway, to access their work computers to accomplish their work. Usually Remote Desktop works great – it’s been tuned well and offers good performance. Sometimes it doesn’t and that’s when […]
-

How to Prevent, Detect, and Remove Spyware
Spyware is a type of malware that hides deep inside your computer. Unlike more visible types of malware, spyware lets you go about your tasks while secretly recording information—especially passwords and other sensitive credentials. Since spyware is difficult to notice, both home users and system administrators need to prioritize its prevention and detection. Thankfully, […]
-

How to Implement a Strong COVID-19 Cybersecurity Plan
As COVID-19 forces more employees to work from home, companies are reevaluating their cybersecurity plans to place an increased emphasis on securing remote access, as well as phishing and ransomware prevention. Here are some of the most important security basics to include in your COVID-19 cybersecurity plan. Secure Remote Access Employees working […]
-
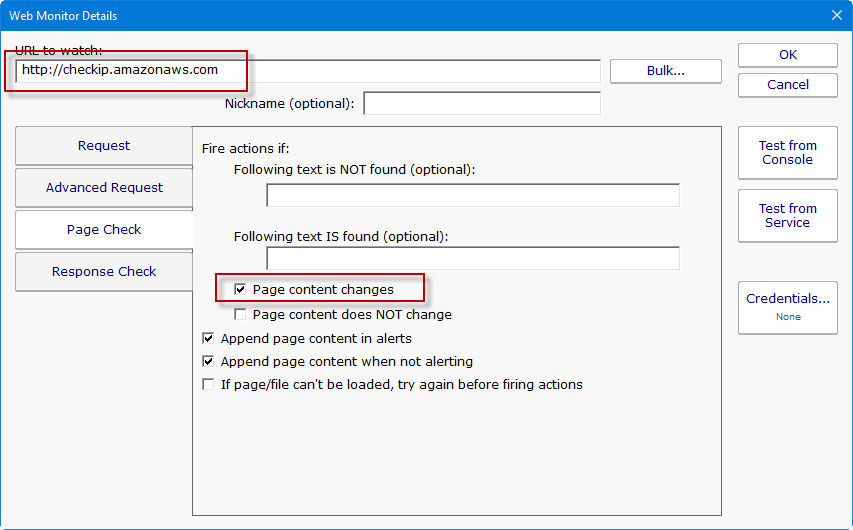
Get Alerted When Your External IP Address Changes
We have the most clever customers 🙂 One customer setup a Web Page monitor to watch http://checkip.amazonaws.com which simply returns your current external IP address. The monitor can alert if the returned data changes so that makes it super easy to find out if you address changes. You could even have it run […]
-

Introduction to Database Security: Security Basics You Need to Know
Database security is essential to keep your business’s data and files security from others that do not need access. Whether you are a small business owner or are a database administrator for a medium or large company, you need to have a solid understanding of data security basics. Why Is Database Security Necessary? Database security […]