Recently we had a case where the SNMP Trap Monitor was truncating text from the received trap. The customer captured some example SNMP Trap packets using Wireshark![]() , and then sent us the capture file. Wireshark is an awesome application to look at network traffic and we highly recommend it.
, and then sent us the capture file. Wireshark is an awesome application to look at network traffic and we highly recommend it.
But back to the network capture – we had to figure out how to replay it, and since it came from a different network, we needed to direct the SNMP Traps to our PA Server Monitor server so it could receive and process them.
It turns out the type of software to use is called a network traffic generator. After looking at many options we settled on the Ostinato packet generator![]() . It has a friendly GUI and lets you change any field in any protocol layer. It is very powerful yet still flexible and easy to use.
. It has a friendly GUI and lets you change any field in any protocol layer. It is very powerful yet still flexible and easy to use.
In our case, we only needed to redirect a few individual UDP trap packets. Before we could load the packet capture, which was in pcapng format (from the Next Generation PCap), we needed to convert it to the older pcap format. Luckily the pcapng.com website has a simple online converter for this.
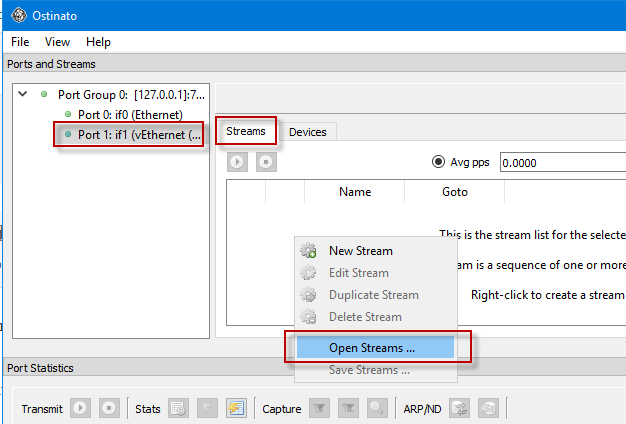
With our capture file in the correct format, it was time to load it. You do that by selecting a network interface, and then going to the Streams tab and right-clicking to load a new stream. When we were done, we had 10 SNMP Trap packets loaded (our customer did a nice job of filtering the capture in Wireshark to just the SNMP Trap packets that we needed).
Once we had the packets loaded we clicked the gear icon on the first one and went to the Protocol Data tab. Here you can change fields for any layer of the protocol stack. In our case we wanted to point the packet to our own server when we replayed it, so we changed the following fields:
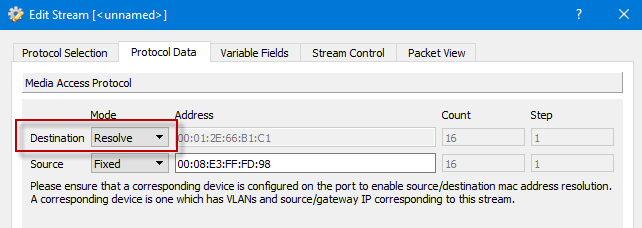
- On the “Media Access Protocol” panel we changed the destination to Resolve, figuring it would pick up the IP address from the other protocol layers.
- On the “Internet Protocol ver 4” panel we changed the Source and Destination IP addresses to be what we needed to target for our network. Important: Be sure to uncheck the “Override checksum” – you don’t want the original checksum but rather want Ostinato to compute a new (correct) checksum for you.
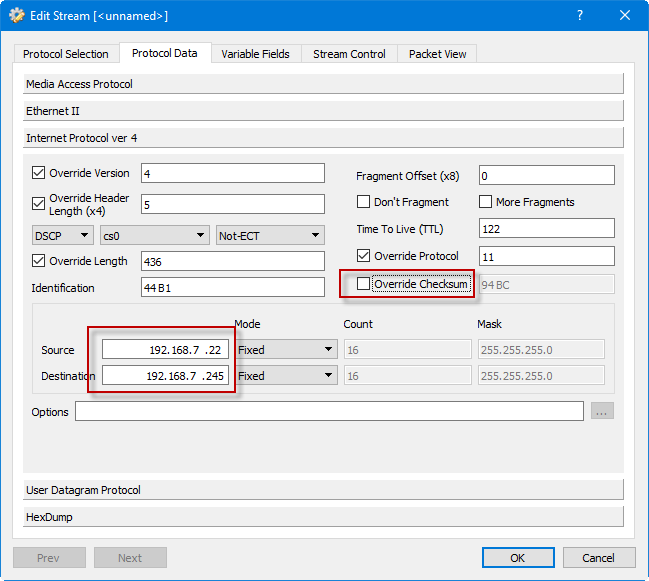
- Similarly, on the “User Datagram Protocol” panel, uncheck the Override Checksum box so the UDP layer also computes a correct checksum for you automatically.
-
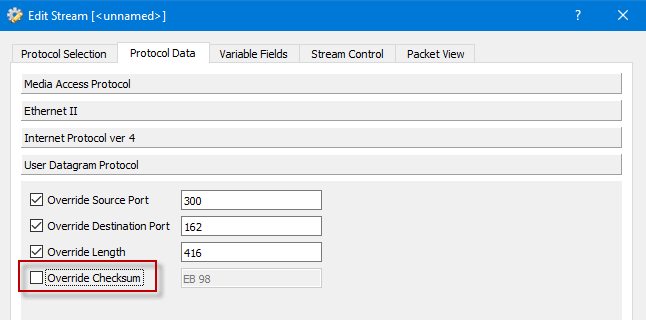
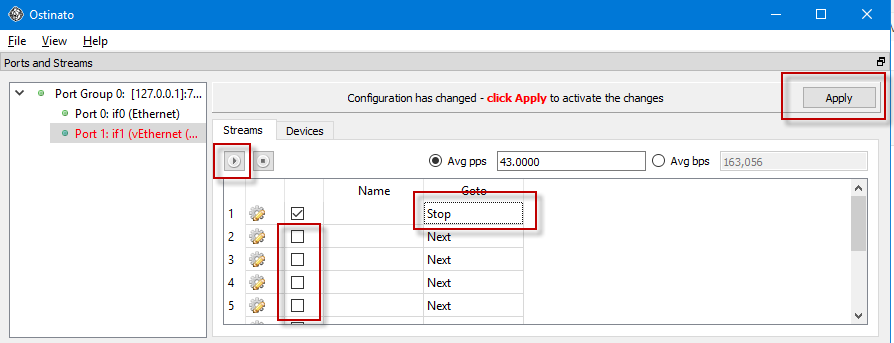
Now that we have our packet set up how we like, it’s time to tell Ostinato what we want replayed. We unchecked all but the first packet. It probably wasn’t necessary, but we double-clicked the Next drop down item and changed it to Stop. And very importantly, click the Apply button. Even though it was highlighted in red, we missed it the first few times and wondered where our packets were 🙁
With that set, you press the standard play button, and Bob’s your uncle! If you wanted to play multiple packets, you can control how often they are fired with the “Avg pps” setting. Note that after changing ANYTHING, be sure to hit that Apply button!
Once we could see the same packets that our customer was seeing, we were able to quickly see where the truncation was happening and get a fix out to them.
Overall we’re quite pleased with Ostinato for packet capture playback.