-

7 Tips to Prevent Ransomware
Ransomware is a malicious type of software that’s used to extort money from victims. It almost always promises to restore the data it encrypts or the operating system it locks, in exchange for a large sum of money. Networks seem to face threats from all directions, but there are ways to prevent malware attacks. Specialized […]
-

Data Loss Prevention and Security Basics You Need to Know
Cyberattacks are the “buzz word” that you hear when a company’s data has been breached. Sometimes the breach results in data being released on the internet. Other times, the hacker holds the data ransom in exchange for a large monetary payout. Data loss prevention and protection should be at the top of your list. […]
-

Remote Access Methods: Monitoring Work from Home and File Access
Working remotely has grown over the past several months for many organizations. The ability to provide remote access involves being able to control access to network and cloud-based servers while allowing employees to access the data and files they require to do their jobs. Remote access is also needed to monitor what data and files […]
-

Data Security Management and Control 101: What Is Data Loss Prevention?
Companies and businesses of all sizes collect and save all types of data. This data can be valuable to others if it were to be leaked outside the business. Data businesses collect can include: Customer Information: The names, addresses, and phone numbers of customers. Purchasing/Ordering Information: The purchase and order history of customers is often […]
-

Server Monitoring and Alerts – Getting Past Common Obstacles
Keeping a server running optimally on a consistent basis involves managing multiple system elements simultaneously. Automated scripts and specialized software can handle the tasks your server needs to complete on a daily basis—but when one of these experiences an error, it can throw the entire system off. Monitoring makes up for other programs’ error-handling […]
-

Monitoring 101: Collecting the Right Data
When it comes to business, data is everything. Whether it’s sales, supply, marketing, or your I.T. systems, every day is a constant stream of decisions to be made. To make the right decisions, you need enough knowledge. To have enough knowledge, you need the right data. What’s the best way to collect all this data? […]
-
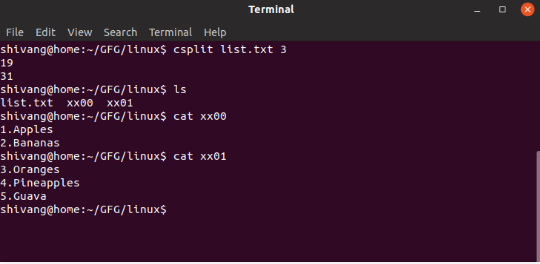
How To Use The Linux Split Command
Linux systems provide a simple command known as split, which enables you to break large files up into smaller pieces. In this guide, we’ll be discussing the syntax, and giving some practical examples of its use. Why It’s Sometimes Necessary To Split Linux Files Some online storage sites put a maximum limit on […]
-

How To Migrate Your Computer To Windows 10 1903
As with Win 10 Home, Windows 10 Pro users (who include Education, Enterprise, and other subscribers) should begin by making a system backup. You’ll then have to set up a feature update deferral. Using an administrator account, click Start > Settings > Update & Security. Then click Advanced Options at the bottom. The […]
-

VPN vs. Remote Desktop – Gateway Security Concerns
VPNs and Remote Desktop Gateways are two different tools used to achieve similar goals. That is: access content or software remotely and securely, and improve the overall freedom of the user – whether that’s from prying eyes or the need to have physical access to their business network. But while each option can be […]
-

How To Keep Track Of Your Android Applications
Keeping track of application usage and the installation of software on your Android phone or tablet is an essential activity, both for device management and your overall security. In this regard, it’s also advisable to monitor how your Android applications are tracking you, in terms of your physical location, activities on the local device, and […]
Got any book recommendations?