Category: Power Admin
-

OpenSSL v3.0.0 – v3.0.6 critical vulnerability
OpenSSL is the backbone of secure Internet communication. It has two currently active and supported development branches: version 1.1.1 and version 3.0. It has recently been discovered that all current versions of OpenSSL 3 (3.0.0 through the current 3.0.6) have a critical security vulnerability, and must be upgraded to a new version immediately. […]
-
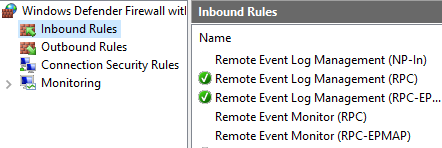
Event Log Monitors Failing? Check Windows Firewall
In the past week or two we have been receiving a lot of email from customers reporting that their Event Log Monitor has suddenly started failing on a number of servers. We don’t have proof, but we’re guessing a recent Windows Update must have disabled the Remote Event Log Management rules. (Edit): Confirmed! Thanks […]
-

What Should You Do When You Receive Event Log Monitor Alerts?
When you are installing PA Server Monitor, you will need to configure what occurs when there are event log monitor alerts. You typically set this up during the initial install. However, it is not uncommon to want to make changes and updates or even add new events to your server monitoring software as you become […]
-
Which Event Log Events Should You Worry About?
When you are configuring your event log monitor settings, you need to decide which event log events you need to worry about. Event logs are generated for a wide array of processes, applications, and events. Logs will record both successes and failures. As such, you need to decide what data is most vital and needs […]
-

How to Configure PA Server Monitor to Monitor Your Event Logs
Did you know that you could configure PA Server Monitor’s Event Log Monitor feature to monitor one or more of your event logs? The event logs can include standard application, security, and system logs, as well as any custom event logs you want to monitor. With our server monitoring software, you have complete control and […]
-

What You Need to Know About Server Security in 2021
How often do you check your event log monitor for potential security breaches? Did you know that many potential security breaches, events, and other problems are logged to event logs? Unfortunately, even the most skilled IT professionals have a hard time making sense of what to watch for that could indicate security issues or even […]
-

How Can an IT Server Monitoring Service Improve Your Net Profits?
You might not think that an IT server monitoring service would have an impact on your net profits. IT-related costs often fall under operational expenses. As such, you have better control over these expenses and can look for different ways you can cut costs without affecting results. Before we get to reviewing some of […]
-

How PA Server Monitor Can Monitor CPU Temperature
High CPU temperature is a common issue with laptops and desktops, and it shouldn’t be ignored. If a computer system routinely generates high temps—above 80°C is usually considered undesirable—it can begin experiencing poor system performance. Over time, heat may progressively damage CPU components in addition to causing the system to lock up or shut down. […]
-

Why Full Reporting Capabilities for Your Databases and Files Are Helpful
Do you know what files your employees access to? Do you know when they create new files? How about when they copy, move, or delete files? How confident are you that your databases are safe and secure from potential intrusions? These are the types of questions any business owner should ask themselves, especially now. […]
-

Supply Chain Safety – Our Measures
The IT world has been in shock as we’ve all learned about the Solarwinds hack (UPDATE: And now also the Kaseya hack). Network and server monitoring software inhabits a special niche where it often has full access to the servers and devices on the network in order to monitor all internal resources. Because of this […]