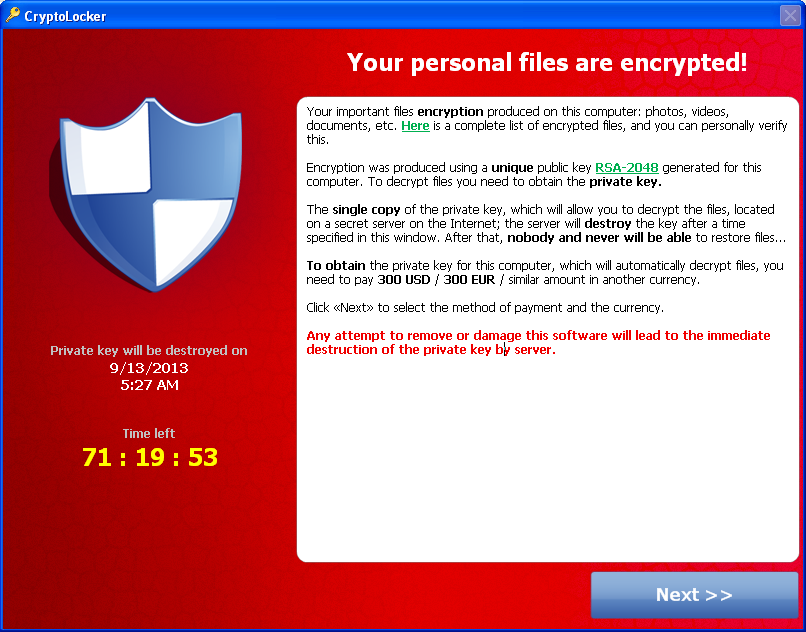
If you spend a lot of time online, are pretty tech savvy or are in the technology sector, then there’s little doubt that you’ve come across the term ransomware here and there. In a nutshell, ransomware is a type of malware that infects a computer and effectively puts up a lock screen that holds the user to ransom – hence the name.
These can be carried out by out and out trickery, as we’ve seen with the Microsoft ransomware scam![]() . This particular scam varies around the world, sometimes the caller tells the computer owner that their machine is infected and they must pay over the phone to remove it (very common in all types of ransomware), whilst at other times, a warning screen pops up with one of the following, or similar:
. This particular scam varies around the world, sometimes the caller tells the computer owner that their machine is infected and they must pay over the phone to remove it (very common in all types of ransomware), whilst at other times, a warning screen pops up with one of the following, or similar:
- A message purporting to be from the FBI/Government/IRS of a threatening nature warning that you have been caught doing something illegal online and must pay an immediate fine
- A message that says you have an infected machine and gives a link to pay to have it removed
- An email that contains a zip file
What sets Cryptolocker apart?
The clue here is in the ‘Crypto’ part of the word. The malware arrives usually in the form of an email, which is often associated with customer complaints, IRS alerts and such like. What they do always have is a zip file. These should never be opened under any circumstances, but it’s not always the easiest thing to keep staff fully in the loop with the latest threats and unfortunately, social engineering fools too many, even now. It can also affect a machine through clicking on an infected link too.
It’s the way that Cryptolocker encrypts these files that sets it slightly apart, as it’s cleverly done. The malware itself also begins to start generating ‘random’ domains names once executed. It does this in order to be able to contact its command and control server![]() , with which it then communicates with through ordinary HTTP POST requests.
, with which it then communicates with through ordinary HTTP POST requests.
The communication that takes place then between the C&C server and the host machine is encrypted by a public key, so it doesn’t necessarily appear to be anything sinister on the face of it, but the C&C server is actually communicating with the attacker’s server.
Once this has been established, the malware will then look for additional files on the victim machine/network and encrypt the results using an AES algorithm. It also adds the line:
HKEY_CURRENT_USER\Software\CryptoLocker\Files registry key into the host machine’s registry.
Isn’t this just something for home users to worry about?
Most definitely not. While of course it affects home users, primarily, the malware targets files that are most commonly used by businesses. It ignores common file types such as photographs and such like that are more commonly found on home machines.
The problem is, once the data has been encrypted it’s not possible to decrypt it, so the best thing to do is restore from a back-up once the affected machine has been cleaned. Of course, there are already tools out there that can help in the clean-up process, but this approach is reminiscent of horses and bolted doors, no use locking up after the damage has been done.
Prevention with monitoring software
By employing monitoring software, this type of problem could be the difference between an IT disaster and a tiny hiccup, if even the latter occurs. Of course, different networks and set-ups will have differing needs, but for the most part, prevention is far better to deal with than cure.
From monitoring server event logs, to actual files and changes that occur on all levels of the network, monitoring software in this case can alert you to a problem before it becomes a disaster. You’re then in a stronger position to limit the damage and stop the malware before it does too much damage.
Of course, it’s always wise to have a policy on opening zip files in a company, as most malware is hidden inside as an executable, which means it can install itself onto the target machine and spread quickly. Saying that, some malware has the capability of looking like a Word or Excel file, so this is where monitoring software may be able to detect the threat before it becomes a problem.
Fighting cybercrime is down to us all
We all have a responsibility to try to keep the net a safe place and that just doesn’t mean businesses. Malware, cybercrime, cyber espionage, all terms that we’re becoming increasingly familiar with and why? Because cybercriminals are ahead of the game when it comes to making millions online. Unlike the old days, when you had to be at least a hacker with some programming knowledge, it’s now as simple as buying a kit on the black market. These are commonly known as exploit kits.
So as well as employing strategies such as hardware firewalls, alongside anti-virus software, it pays to invest in monitoring software for your network, however large or small, to ensure that the risk is mitigated.
It’s also a good idea to train your employees on the risks that are available, even if it means sending them to a workshop or investing in an LMS. Many businesses are ill-prepared for common audits, let alone attacks on the network. This means potentially, malware such as Cryptolocker can mean the loss of revenue and data and even lead to a large fine if you deal with consumer information, such as credit cards.
Don’t let your business fail an audit, or get attacked – Contact Us today to see how we can help today.