Everyone knows you need to protect against hackers. How do you protect your computers from hackers? One way is to monitor for lots of failed login attempts. But how do you do that?
Everyone knows you need to protect against hackers. How do you protect your computers from hackers? One way is to monitor for lots of failed login attempts. But how do you do that?
With Windows, you watch the Security Event Log – there are many, many events related to users logging in, failing to login, accounts getting locked and so on. And the events change every once in a while based on the version of Windows you’re using. Great! (not)
To get started, you’ll need some sort of Event Log Monitor such as we have in PA Server Monitor. (And if you hold on, I’ll show you an even easier way at the end of the article!)
Specifically, you need to watch the Security Event Log, and the Security event source for Windows 2003, or the Microsoft Windows Security Auditing event source for Windows 2008 and newer.
Each event within an event source has a unique ID (note that IDs are not unique among sources), so you need to watch for specific events that pertain to the condition you want to watch for. For example, to watch:
| Event To Watch | Event IDs |
| Failed Logon because of bad password | 4625, 529 |
| User Account Locked Out | 4740, 644, 6279 |
| User Account Created | 4720, 624 |
You’ll note there is more than one Event ID for each of these. In general, 4-digit Event IDs are for Windows 2008 and newer, and the 3-digit Event IDs are for Windows 2003.
There are many, many more than this. Randy Franklin Smith has a nice quick reference available from here![]() .
.
Once your monitoring system finds your events, you will probably want to do two things: alert, and write them to a database for later reports.
Alerting is pretty easy. Writing the events to a database is harder than you might think. You see, there are more than 100 Event IDs that are probably worth watching. And most of them have a different layout, which means if you want to get the username from an event, it shows up in different places in the text. Sometimes the computer the user is on is shown and sometimes not. Some events are about group properties being changed and a user account isn’t mentioned. That means you have to come up with a way to parse out the data you care about in each of those events before you can save it to the database. That is the hard part.
There is one other thing you need to do: ignore the noise accounts. Windows computers often talk to each other, and when they do, they use “Machine Accounts”. These are the computer name with a $ at the end. So if SERVERA connects to SERVERB for some reason, it will do it as machine account SERVERA$. There are other accounts to ignore as well. Modern versions of Windows often have a “Window Manager\DWMx” account that logs in when a user does. Those are not interesting. And finally, there are sometimes anonymous ‘logins’ in some events that can be ignored.
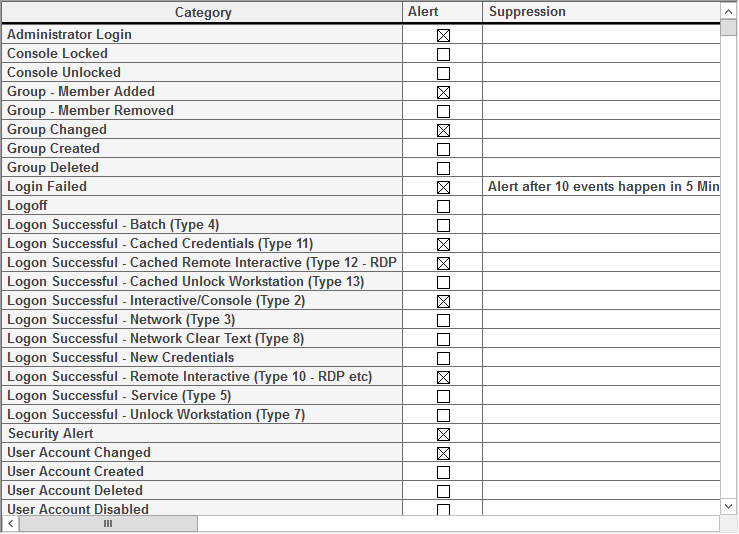
This ends up being a lot of work. It would be really nice if someone would write a simple to use Active Directory Login Monitor that would do this for us. Something like what is shown below.
Hmmm… That looks pretty easy to use 🙂 If you think you might like an easy to use Windows Active Directory Login Monitor, that can do things like alert you when an administrator logs in, or a login has failed X number of times, give PA Server Monitor a try!