Category: PC Security
-

Russian Hackers and the DNC – Email Security Matters
Robert S. Mueller, Special Counsel for the US Department of Justice, has just released his findings about the Russian Hacking of the Democratic National Convention in 2016. It’s a very interesting read containing information on how the hacks took place (spearfishing, spoofed emails, spoofed websites, bitcoin mining to obscure payments, etc). If any corporate […]
-

Keeping Your Account Safe From Hackers
Internet use, cloud and remote working, along with e-Commerce, are still booming – and any type of online presence is an excellent way to increase your organisation’s operational effectiveness, visibility and scope, boost sales, grow your client base and enhance your reputation. The internet has offered us the possibility to work wherever we choose, keeping […]
-

5 Phone Security Mistakes you’re probably making
In this enlightened technological age, we all think we’re clued up on tech security, don’t we? We know to secure our PCs and laptops with passwords, two-step verification, anti-virus software, firewalls and anti-spyware and keep a check on our browser security settings. We’ve read the data breach horror stories and the torrid tales of hard […]
-

How to check for MS17-010 and other HotFixes
Sometimes you need to check on the status of your applied updates and quickly. With news of the WannaCrypt/WannaCry Ransomware spreading via the MS17-010 vulnerability around the globe it’s a good idea to double check that all your updates are applied correctly. The following is a quick PowerShell Execute Script monitor that you can add […]
-

Making the most of Office 365 Security tools
Moving to a cloud based service such as Office 365? Many organisations contemplating a move to a cloud based service are rightly concerned about security. With new threats being introduced on a regular basis, organisations need to use all the tools they have at their disposal to secure their data. Official Government Guidance on the […]
-

5 Great Ransomware Removal Tools
Ransomware is one of the fastest growing security threats in the online world. Over the last few years, ransomware attacks have become increasingly common to the extent that these attacks have evolved into one of the most harmful forms of cyber attack there is. Ransomware attacks can target any PC user, whether it’s a […]
-

Top Windows 10 Security features
Windows 10 has introduced a range of new security features to combat some of the issues faced by previous Windows operating systems. Here we run down on the top features available for your protection Malware Protection Device Guard, the primary tool for fighting malware in Windows 10, only allows users to download trusted applications that […]
-
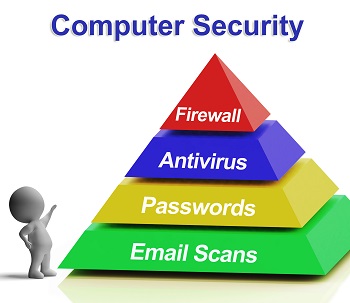
The Importance Of Layered Network Security
As enterprises look to streamline their operations by integrating the diverse aspects of their business and using networked computing architectures to provide a consistent platform and medium for this to take place, their need to guarantee the security of these networks becomes that much greater. In today’s environment, breaches, bottlenecks or downtime leading to the […]
-

Monitor (Failed) User Logins in Active Directory
Everyone knows you need to protect against hackers. How do you protect your computers from hackers? One way is to monitor for lots of failed login attempts. But how do you do that? With Windows, you watch the Security Event Log – there are many, many events related to users logging in, failing to […]
-

How Cyber Attacks Affect Us
Another nice infographic from Utica College. . Source: Utica College Cyber Security