Category: PC Security
-

Enterprise Encryption Best Practices
Whether it’s to safeguard internal protocols and hierarchies, or to guard against attacks and data breaches in the escalating scale of current cyber-threats, implementing controls on the way information is transmitted and shared is more crucial to the enterprise than ever. Encryption has been and remains an essential aspect of this process. But how best […]
-
Enterprise Encryption Best Practices – Info Graphic
We hope you like this infographic. We’ll have a follow up article posted on October 18th with more information 🙂
-

15 Ways to Protect Your Business from Hackers
Today we have a guest post from Sachin over at FromDev.com. And without any further ado, we’ll turn it over to Sachin. There is no business in this internet age that cannot be hacked. Most skilled hackers can hack into any system. It has happened to most of the top tech businesses in the past, […]
-
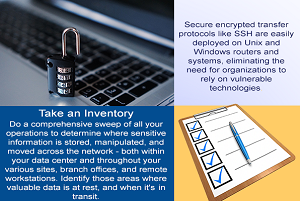
Endpoint Security Tips
With BYOD (Bring Your Own Device; either personal, or provided by the enterprise) now an integral part of policy in so many organisations, there’s an increased risk of USB flash drives, laptops, tablets, or smartphones holding sensitive data falling into the wrong hands – or being compromised in some way that allows malicious intruders to […]
-

Over the Edge?
As desktop and mobile owners continue to make a slow transition from previous versions of the operating system to Microsoft’s new Windows 10, enough user experience and feedback has emerged to give so me early assessments of the software giant’s flagship environment. In this article, we’ll be looking at one of the linchpins of […]
-

Network Security: How to Avoid Physical Security Threats
In a 2015 study conducted by Ponemon Institute, a data security research organization, they found that the average total cost of a data breach incident was $3.8 million. In 2014, the average cost was only $3.5 million. In recent years, data breach has become increasingly common that many companies are stepping up their IT security […]
-
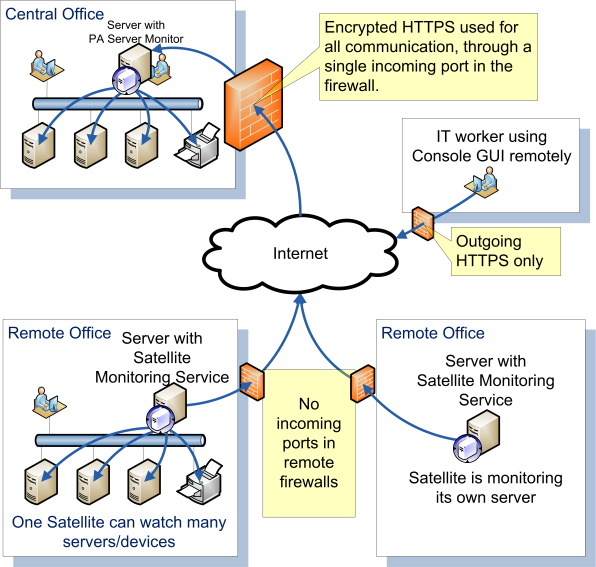
Free and Secure Remote Access? Sort of …
Recently, GoToMyPC forced all customers to reset their passwords. They were not hacked, but rather saw that hackers were attempting to access their customers’ computers using credentials that had been hacked from other places. This seems like a good opportunity to show off how PA Server Monitor can allow remote access in a completely […]
-

Reducing the Risks of File Sharing
Exchanging ideas and sharing information are integral parts of working life. Ever since computers and digital technology became central to the way we work, people have exploited various means of passing documents and files containing text, images, and audio-visual data on to colleagues, suppliers and partners. As technologies have evolved, the methods have improved. […]
-

Another email Hack: Should We Worry?
Each time a major email service or social media platform gets hacked, the incident generates exciting headlines in the media. But behind the hype there’s a very real tale of anxiety for all the users concerned. Has vital information been stolen or compromised? Are funds being siphoned off, into the hands of criminals – […]
-

What is Cryptolocker Ransomware?
Cryptolocker is a well known malware (software that does harm) of a particular variety: ransomware. Some malware (like computer viruses) delete and destroy. The hackers that create ransomware have other motivations: money. Ransomware Ransomware does something to your computer, and then demands a ransom payment to get your computer back to the way it used […]