Author: Zoë
-

Why Your Internet Browser is Such a RAM Hog
By Des Nnochiri Savvy computer users have been ranting for years about how their internet browser hogs so much of their RAM. The issue has become so important that some are even using a platform’s RAM-consumption rate as the main factor affecting their decision to use it. Although shocking that a single application on […]
-

Tips on Security Risk Assessment
By Des Nnochiri Performing a security risk assessment has become an economic and functional necessity in the digital economy. Cyber-threats and many of the legal and operational aspects of data-handling now constitute as much of a challenge to enterprise success as effective marketing, and continuous service delivery. A strong security posture, responsible data […]
-
Number of Exceptions Thrown Counters
-

The Sound of Silence: Threats from Without and Threats from Within
By Des Nnochiri Recent news has broken about a group of hackers which appears to be operating out of Russia. The group, dubbed “Silence,” is believed to be involved in the theft of over $800,000 from multiple Russian and Eastern European financial institutions. However, what is particularly notable about this group is they […]
-
Here’s How to Stop Google from Tracking Your Phone – For Real This Time
By Des Nnochiri We all know Google wants to be in all our business. Whether we’re shopping, streaming, searching, or taking a stroll, Google is gathering vast amounts of data on us through our ubiquitous smartphones and other connected devices. However, up until recently, you may have thought that if you disabled your […]
-
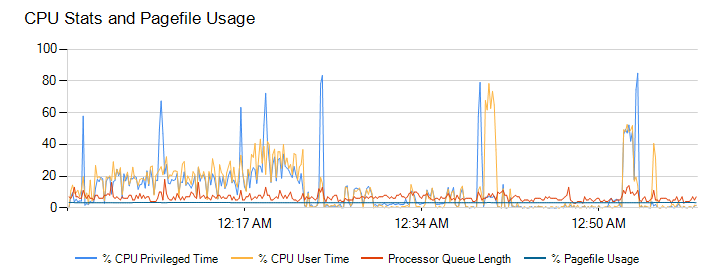
Paging File Percent of Usage Counter
By Zoë Dunning Following last week’s article about monitoring CPU usage using Performance Monitor counters, this post concerns the “\Paging File\% Usage” counter. Overview “\Paging File\% Usage” displays the percentage of the paging file that is currently in use. A paging file is a hidden, optional system storage file on a hard disk. Only […]
-
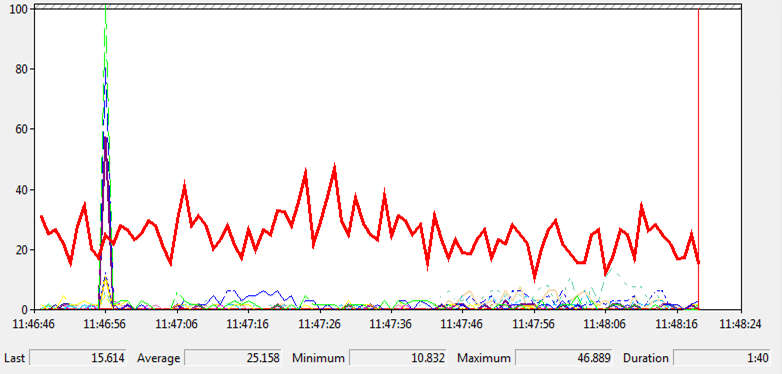
Counters Monitoring CPU Usage
By Zoë Dunning This week’s topic is monitoring CPU usage using the “\Processor Information(_Total)\% Processor Time” and “\Processor Information(_Total)\% Processor Queue Length” counters. Overview “\Processor Information(_Total)\% Processor Time” shows the percentage of the time that the processor takes to execute a non-idle thread during a sample interval. In other words, this counter shows processor […]
-

GDPR Compliance Auditing Tips
By Des Nnochiri Now that the General Data Protection Regulation (GDPR), drawn up by the European Union (EU), has finally come into effect, many of the affected organizations have been scrambling to keep up with the auditing and operational requirements of a compliance regime that’s widely recognized as one of the most stringent and […]
-

The Connected Home – How Secure Are All These Gadgets?
by Des Nnochiri Connected or smart homes are becoming more commonplace as people use computer networks to control different aspects of their in-house technology. But how secure are these networks? Everything Online A connected home allows occupiers to remotely control and monitor their in-house technology via their smartphones and tablets and its uses can […]
