Author: Dan Popescu
-
Configuring a Public Key Infrastructure-Pt. 2
Part 2, Continued from “How to Configure a Public Key Infrastructure on a Windows Server – Part 1” Enable the policy and check the Renew expired certificates, update pending certificates and remove revoked certificates and update certificates that use certificate templates check-boxes: Now we have to configure certificate templates for auto-enrollment. Open the Certification Authority […]
-
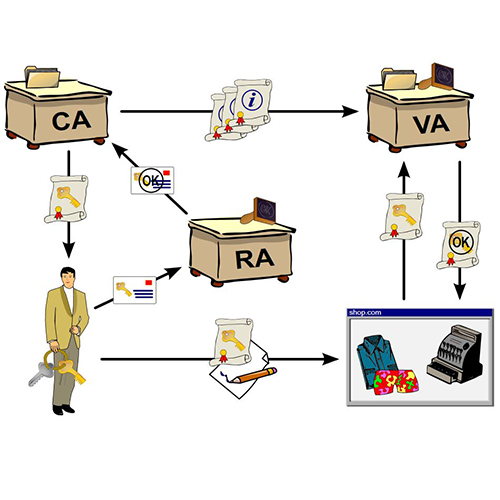
How to configure Public Key Infrastructures
In today’s article we will discuss implementing a PKI (Public Key Infrastructure) on a Windows Server 2008. The PKI will be used to authenticate wireless users. Note that the steps indicated here can also be applied to Windows Server 2012 versions. Before proceeding to the actual practice example, we’ll have to get acquainted with the […]
-
Encrypt Hard Drives Using BitLocker Drive Encryption-Cont’d
Part 2… From previous experience I can tell you that this operation can take several hours if your hard drive contains a lot of data, so make sure that the laptop stays on until the encryption is complete. Upon finishing the operation, you will receive the following message: If you are encrypting a system […]
-

Encrypting Your Hard Drive Using BitLocker Drive Encryption
In this article, we will talk about one of the most effective and powerful encryption mechanisms available with Windows Systems. BitLocker is a feature that enables you to encrypt your hard drive data so that it becomes practically impenetrable by hackers. This means that even if your portable device gets in the wrong hands, without […]
-
Tips 8-12: How to Optimize and Speed Up Windows 7 Performance
Cont’d from… “Top 12 Tips: How to Optimize and Speed Up Windows 7 Performance” #8. Uninstall any unwanted program I recommend that you uninstall any unused programs from your computer. By doing this, registry keys are cleaned, hard disk space is increased, running processes are reduced and overall computer’s performance is increased. You can uninstall software […]
-

How to Configure DNS Client Settings
In this article we will discuss some of the DNS settings that each workstation must be configured to in order to communicate within a computer network. DNS is one of the most important services that run within a network or even in the Internet. The infrastructure of the Domain Name System can differ from one […]
-

How to Monitor MS SQL Server
This will be the third in our blog series about monitoring. The first covered monitoring IIS and the second, monitoring ASP.NET. Please take a look at these first to get some basic information about how to monitor different Windows products. In today’s article we will focus on how to use monitoring software to visualize, troubleshoot […]
-

How to Monitor ASP.NET
Last week we talked about how to monitor IIS. Today we’re going to discuss monitoring ASP.NET. We’ll cover a number of things including: the main implications of monitoring ASP.net, the most important performance counters to look for, performance counter values that should be measured and services dependent on ASP.net that should be monitored. If you […]
-

How to Monitor IIS
This will be the first in a series of three blog posts on monitoring. In this article we’ll discuss monitoring Internet Information Services (IIS), the web hosting platform available in Windows Server editions. IIS is very popular in part because it provides such a compact service with lots of features and configurations. Most enterprises that […]
-

Why Is Network Security Important?
As the internet evolves and computer networks become bigger and bigger, network security has become one of the most important factors for companies to consider. Big enterprises like Microsoft are designing and building software products that need to be protected against foreign attacks. By increasing network security, you decrease the chance of privacy spoofing, identity […]