Part 2…
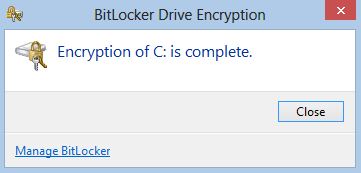
From previous experience I can tell you that this operation can take several hours if your hard drive contains a lot of data, so make sure that the laptop stays on until the encryption is complete. Upon finishing the operation, you will receive the following message:
If you are encrypting a system partition like I did, then every time your computer is started, an authentication password will be required prior to the OS loading screen.
BitLocker is the most effective way to protect your information in case of theft. The encryption mechanism used with this protection feature is AES (Advanced Encryption Standard). AES is a symmetric-key algorithm which basically means that the same cryptographic key is used for both encryption and decryption. The algorithm was developed in 2001 as an enhanced encryption algorithm which is widely used today in different technologies.
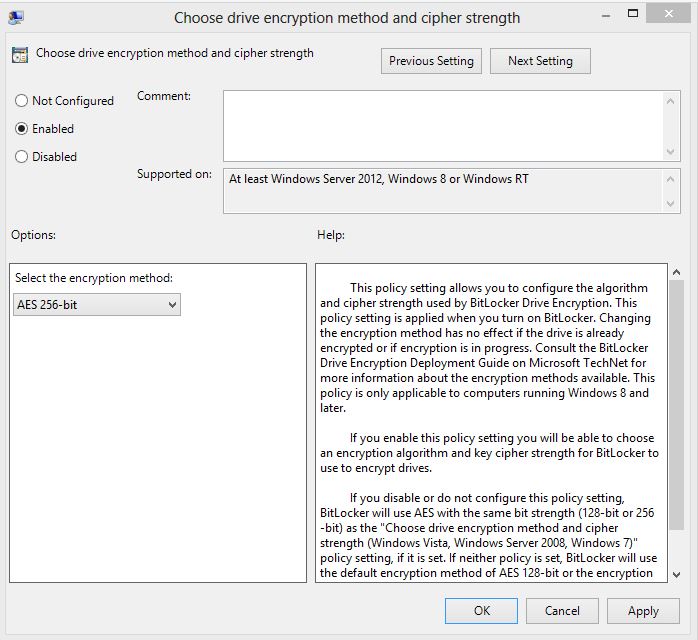
By default, the OS will encrypt information stored on the hard drive using a 128 bit encryption key. If you haven’t changed any policy regarding the BitLocker encryption key then this version will be used. Windows supports also a 256 encryption key when using AES for BitLocker, this feature can be enabled from local group policy console (gpedit.msc). Navigate to Computer Configuration/Administrative Templates/Windows Components/BitLocker Drive Encryption and open the Choose drive encryption method and cipher strength policy. There can be two policies with the same name, one compatible with Windows 8 and Windows Server 2012 and another one compatible with older versions of Windows. Remember that this policy has no effect if you apply it to an already encrypted hard drive or when the encryption is running. If you want to use a 256 encryption key, enable this policy prior to turning on BitLocker:
By using a 256 bit key, the encryption mechanism is enhanced and your device becomes even more secure.
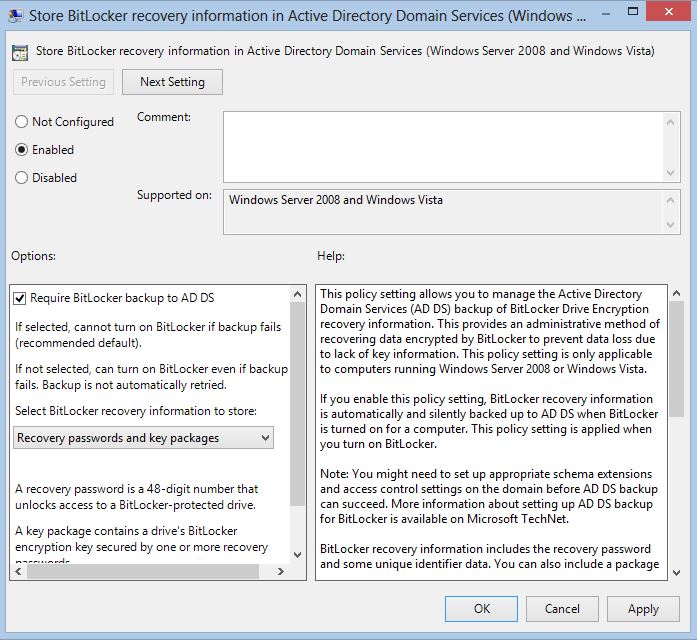
If BitLocker is enabled inside a private domain that is using an Active Directory infrastructure it is recommended that you store the recovery information within AD. The only requirement for this feature to is to enable the Store BitLocker recovery information in Active Directory Domain Services policy. You can select to store either Recovery passwords and key packages or Recovery passwords only:
If you are not using an Active Directory Infrastructure then you can create a default password repository by enabling the Choose default folder for recovery password policy. This policy will not prevent the user from storing the recovery key in another folder but it will be used by default by all systems where this policy is applied. There are multiple policies available in this section like providing a unique identifier for your organization that will be used with each encrypted device or prevent memory overwrite on restart. I like that BitLocker supports a lot of features and policies. You can explore each of these policies in Fixed Data Drives, Operating System Drives and Removable Data Drives sections.
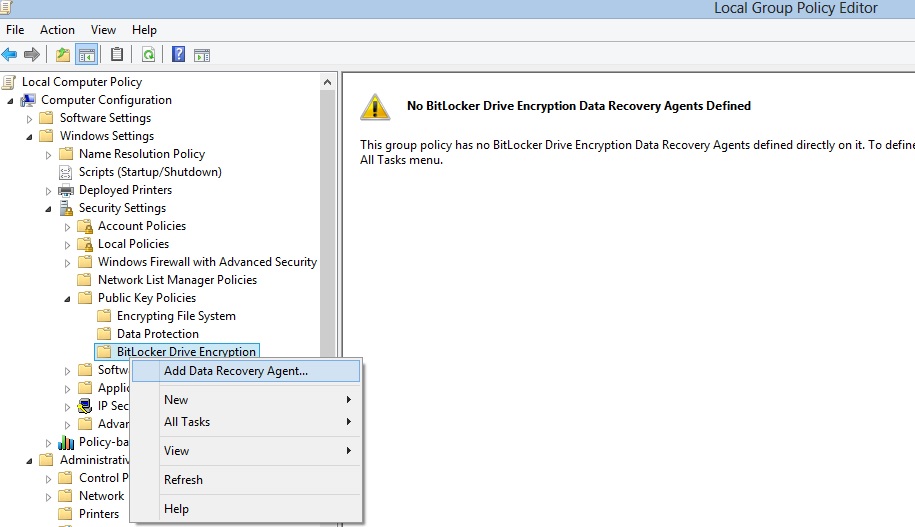
With BitLocker you can also designate users as recovery agents for BitLocker encrypted drives. These recovery agents can decrypt drives using their certificates or public keys. You can add a recovery agent from group policy. Navigate to Computer Configuration/Windows Settings/Security Settings/BitLocker Drive Encryption, right click and select Add Data Recovery Agent:
Note that you’ll have to provide a .cer certificate for the designated users. If you are using an AD infrastructure than you can select the users directly from the database if the certificates are published in the directory.
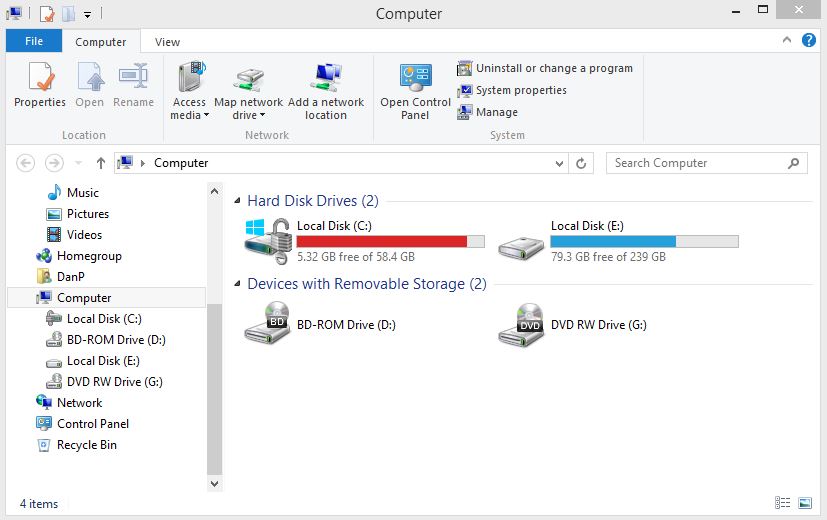
After BitLocker has been activated on a System drive and the encryption is completed, this is how will the OS partition look like compared to an unencrypted drive:
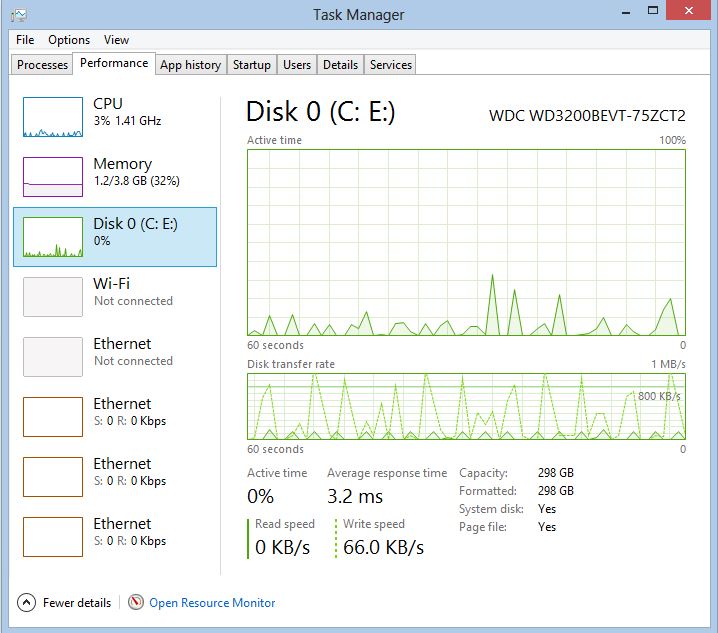
I’ve read from different sources that BitLocker can increase your resource utilization when it’s enabled. Personally, I’ve enabled this feature on all my portable devices and not one had high usage because of BitLocker. I’ve encrypted drives that were almost full and didn’t have any issues with them. This laptop has an I5 CPU M430 @2.27 Ghz with 4 GB of RAM and this is how the usage graphics look:
Personally I think that BitLocker is one of the greatest security features Windows can offer. If you have a different opinion please add a comment and share your thoughts. I hope this article was informative and has helped you.
P.S. If you have any ideas about articles that you’d like to see on our website please send us an email at… support@poweradmin.com, or simply leave a comment below.