By Des Nnochiri
As with any other operating system, security is a prime concern with Linux network hardware. In this article, we’ll be giving some recommendations on how to toughen the security posture of your Linux servers. Screenshots and example syntax relate to systems running Kali Linux, CentOS, RHEL, Ubuntu, and Debian-based Linux distributions.
Encrypt Data for Greater Information Security
Unencrypted or plaintext data held at rest or in transit across a network is vulnerable to packet-sniffing and extraction. At the very least, data in transit should be scrambled or encrypted, using a strong encryption protocol with keys and/or digital certificates.
File transfers should be executed under secure protocols such as scp, ssh, rsync, or sftp. OpenSSH, SFTP, or FTPS (FTP over SSL) add Secure Sockets Layer (SSL)—or Transport Layer Security (TLS) encryption—to the standard file transfer protocol (FTP). Using special sshfs and fuse tools, mounting a remote server file system or your own secure home directory is also possible.
You can use the following syntax to remove outdated file transfer services such as NIS or rsh from your system:
# yum erase xinetd ypserv tftp-server telnet-server rsh-server
On Debian- or Ubuntu-based Linux servers, the apt-get or apt commands may be used to eliminate insecure services:
$ sudo apt-get –purge remove xinetd nis yp-tools tftpd atftpd tftpd-hpa telnetd rsh-server rsh-redone-server
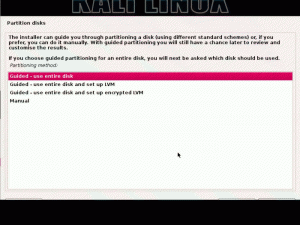
For data at rest, most Linux distributions will allow you to encrypt your hard drives before installation. On Kali Linux, choose the options “Guided-use entire disk” and “set up encrypted LVM” to set up your encrypted logical volume manager.
(Image source: Network World![]() )
)
Isolate Network Services
To limit the number of other services that could be compromised by a security breach, Linux administrators should run different network services on separate servers or virtual machine (VM) instances. Virtualization software such as OpenVZ may be set up as a separate install on RHEL and CentOS Linux distributions.
To further secure your host network on Kali Linux, you can take the following steps:
- Disable IP Forwarding by setting the ipv4.ip_forward parameter to 0 in “/etc/sysctl.conf”
- Disable Send Packet Redirects by setting the ipv4.conf.all.send_redirects and net.ipv4.conf.default.send_redirects parameters to 0 in “/etc/sysctl.conf”
- Disable ICMP Redirect Acceptance by setting the ipv4.conf.all.accept_redirects and net.ipv4.conf.default.accept_redirects parameters to 0 in “/etc/sysctl.conf”
- Enable Bad Error Message Protection by setting the ipv4.icmp_ignore_bogus_error_responses parameter to 1 in “/etc/sysctl.conf”
Keep Software Installations Lean and Up-to-Date
The more applications or web services you have installed, the greater the potential for falling victim to software vulnerabilities or for attackers to compromise your programs. So limit the number of installations you add to the core system only to those applications that are strictly necessary. The apt-get and/or dpkg commands, or a dedicated RPM package manager such as yum, may be used to review all the installed software on your system—and they include commands for removing any unwanted packages or services.
Here’s a syntax example using dpkg and apt-get:
# dpkg –list
# dpkg –info packageName
# apt-get remove packageName
It’s also important to regularly update and patch your software to install the latest security fixes and benefit from the latest tools and features of your applications. On Debian or Ubuntu Linux systems, it’s possible to configure unattended upgrades for your server software using the apt-get or apt commands:
$ sudo apt-get install unattended-upgrades apt-listchanges bsd-mailx
Use Linux Security Extensions
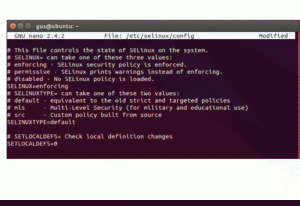
Linux includes a number of security tools![]() that can enforce limitations on networks and other programs and guard against poorly-configured or compromised software.
that can enforce limitations on networks and other programs and guard against poorly-configured or compromised software.
(Image source: Network World![]() )
)
SELinux (Security Enhanced Linux) provides a range of security policies for the Linux kernel, including a flexible Mandatory Access Control (MAC). The mechanism has three configuration modes:
- Disabled: Protection is inactive.
- Permissive: Prints warnings if issues are detected.
- Enforcing: Security policy is enforced.
Running a MAC kernel protects a Linux server from malicious or flawed applications that might damage or destroy the system.
Set a Strong Password Policy
You can use the useradd or usermod commands to create and maintain Linux user accounts. As in any IT environment, the standard criteria for strong passwords apply (eight characters or more, a mix of letters, numbers, and symbols, changed regularly). You can use the change command to configure the number of days between password changes and the date of the last password change.
The passwd command can lock and unlock accounts:
# lock account
passwd -l userName
# unlock account
passwd -u userName
The faillog command displays failed login attempts in the form of faillog records and enables administrators to set login failure limits
Use Centralized Authentication
To guard against the presence of out-of-date credentials and forgotten accounts on a network, use a centralized authentication system. A service such as OpenLDAP for clients and servers allows administrators to exercise central control over Linux or UNIX accounts and authentication data. It also allows them to keep authentication data synchronized between servers.
Kerberos performs authentication as a trusted third-party authentication service. It uses a “cryptographic shared secret” policy, which assumes that packets traveling along an insecure network can be read, modified, and re-inserted. Remote login, remote copy, secure inter-system file-copying, and other high-risk tasks may be performed using symmetric-key cryptography.
Enforce Physical Security Measures
Finally, don’t neglect the physical aspects of Linux network security. These include restricting physical access to data centers and hardware (authorized users, screening, surveillance, etc.). Physical security measures also encompass specific protocols for safeguarding network hardware.
For example, you can disable the booting of Linux servers from external devices such as DVDs, CDs, or USB sticks. To do this, you can set BIOS and grub boot loader passwords so that other users won’t be able to change and override the security settings of the server. You can also access the security settings on the admin page of any internal web servers on your Linux motherboard to change the default passwords and administrative privileges.