NAP or Network Access Protection is a Windows Server security mechanism which enables you to control how computers gain access to network resources. The main functionality of NAP is to verify and ensure that only healthy computers will be marked as compliant and will receive network access. In this article we will talk about some of the enforcement technologies available with NAP. These technologies are responsible for allowing or denying network access for NAP clients. There are four main enforcement types available with NAP as follows: IPSec, DHCP, VPN and 801.2X. Within a network you can configure one or multiple enforcement types and these technologies should be chosen according to the network’s infrastructure and requirements.
DHCP Enforcement
– Uses a Windows Server that has the Dynamic Host Control Protocol (DHCP) service running. Compliant computers will gain network access while non-compliant computers can be either redirected to remediation servers or denied network access. Once you’ve installed and configured DHCP![]() you’ll need to add the Network Policy and Access Services role to your Windows Machine. If you need to configure additional DHCP options, check this article from IT training day
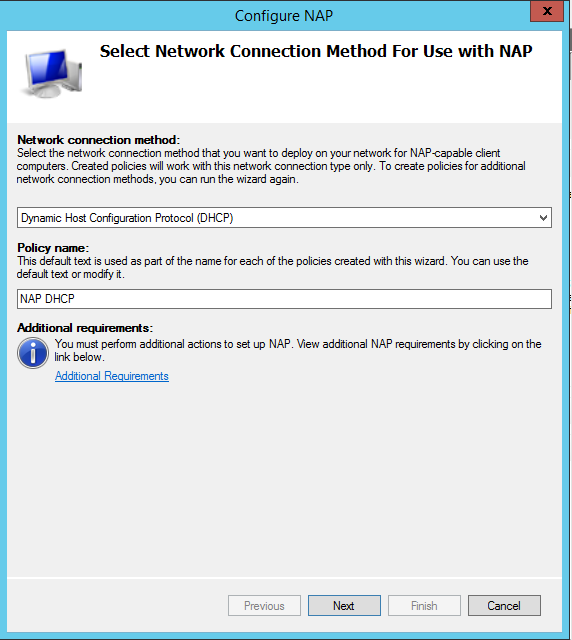
you’ll need to add the Network Policy and Access Services role to your Windows Machine. If you need to configure additional DHCP options, check this article from IT training day![]() . Note that for these demonstrations I will be using a Windows Server 2012 machine. After you add the Network Policy and Access Services role, open the NPS console and configure NAP using the wizard:
. Note that for these demonstrations I will be using a Windows Server 2012 machine. After you add the Network Policy and Access Services role, open the NPS console and configure NAP using the wizard:
If you don’t know how to install and configure NAP using the wizard you should check this link![]() for further instructions. Once NAP has been configured for the DHCP server, you’ll need to enable NAP for the desired DHCP scopes. To enable NAP enforcement for all DHCP scopes, open the DHCP console and navigate to the IPv4 section, right click and select Properties:
for further instructions. Once NAP has been configured for the DHCP server, you’ll need to enable NAP for the desired DHCP scopes. To enable NAP enforcement for all DHCP scopes, open the DHCP console and navigate to the IPv4 section, right click and select Properties:
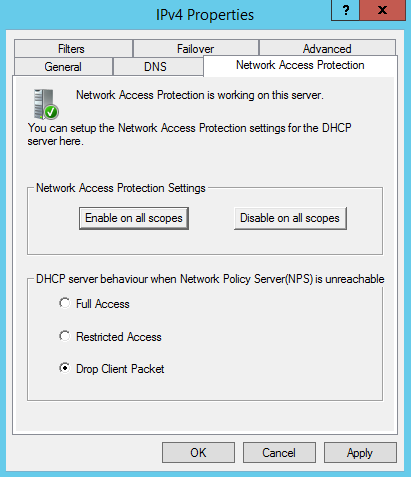
Navigate to the Network Access Protection tab and just under the Network Access Protection Settings section, click the button enable on all scopes. You can configure what behavior the DHCP server takes in case the Network Policy Server (NPS) is unreachable. There are three options available as follows:
Full Access – all NAP clients will receive network access even if they are not compatible with NAP’s policies.
Restricted Access – devices that are not compliant with the network’s requirements will receive access to the remediation servers to fix any problems regarding their health state.
Drop Client Packet – the server will drop the connection with non-compatible NAP clients requesting access to the network.
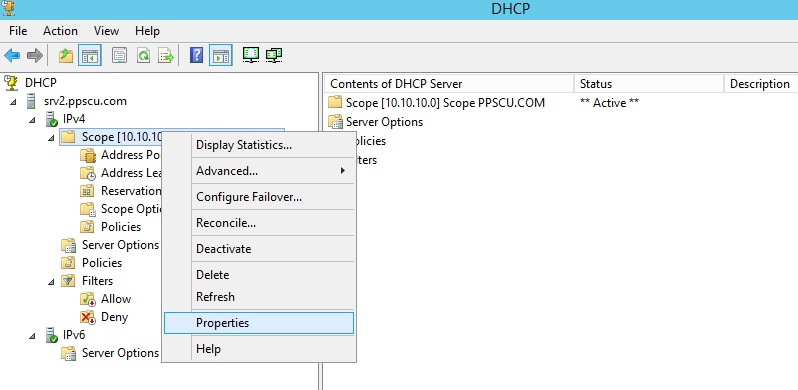
If you want to enable NAP enforcement for a single scope, navigate to the desired scope section and select Properties:
Now navigate to the Network Access Protection tab and enable this feature for the scope. You can use the default NAP profile or use a custom profile.
802.1X Enforcement
– This NAP enforcement takes advantage of 802.1X compatible switches and APs (access points) to authenticate computers. The server running the NPS service will check each computer before it is authenticated and if the health state is not compatible with the network’s requirements, the computer will be redirected to the remediation network. Switches and Access Points use special filters such as ACLs (Access Control Lists) and/or VLANs (Virtual Local Area Network) to separate non-compliant computers from the rest of the network.
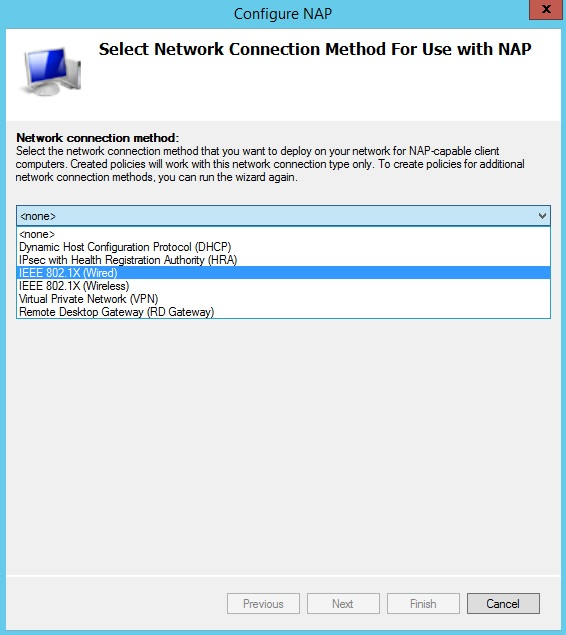
You’ll need to configure NAP for IEEE 802.1X Wired or Wireless networks using the Wizard:
When enabling PEAP Protected Extensible Authentication Protocol for 802.1X NAP enforcement, you’ll need to install a server certificate from a Certification Authority (CA) trusted by the NAP clients. The best thing to do is to enable auto-enrollment on your local CA. If you don’t know how to enable this feature then check out one of our past articles about implementing a PKI (Public Key Infrastructure) using Windows Servers. The wizard will also require you to configure NAP exemptions which basically means group of devices that are not checked for compatibility by NAP’s health validation. Once the wizard is complete, the NAP service will start and your clients will be able to access the network if the NAP validation is completed successfully.
VPN Enforcement
– When NAP is configured for VPN enforcement, it will verify each remote client that is trying to authenticate within the network. There are several steps that you need to take to successfully deploy NAP for VPN. You’ll need to install Routing and Remote Access services and configure it as a VPN server. You will then configure the server running the NPS service as the RADIUS server in Routing and Remote Access.
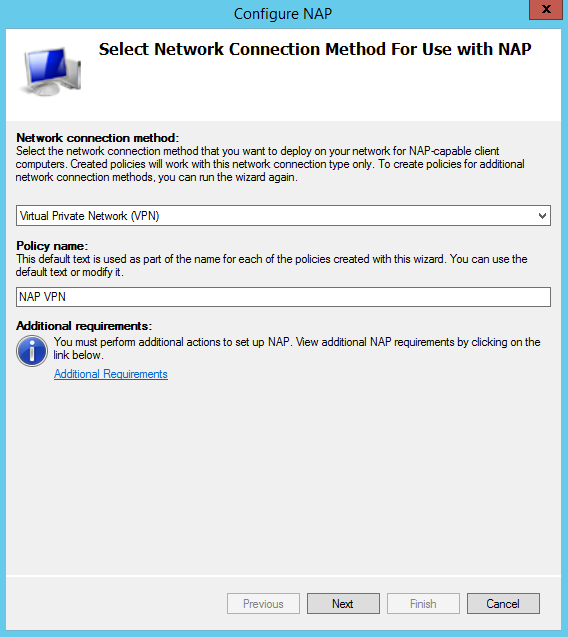
The NPS server will be configured using the Wizard by specifying the Virtual Private Network (VPN) as the network connection method. Also note that In NPS, the VPN servers will be configured as RADIUS clients:
Once the Certification Authority is deployed and the certificate has been installed on the server, the VPN enforcement can be installed.
NAP also supports IPSec enforcement with Windows OS but, it’s a long story and cannot be covered in this article. If you are interested in discovering IPSec enforcement installation and configuration, check out this article![]() . Hope you’ve understood the main principles behind NAP enforcement, share this article to others interested in this topic. Wish you all the best and stay tuned for the following articles.
. Hope you’ve understood the main principles behind NAP enforcement, share this article to others interested in this topic. Wish you all the best and stay tuned for the following articles.
Featured Photo Credit: Alain-Christian![]() via Compfight
via Compfight![]() cc
cc![]()