 VPN or Virtual Private Network has become one of the core components in large enterprises and as a System Administrator you will most certainly stumble upon this technology. There are multiple VPN equipment Vendors, each one with their own features.
VPN or Virtual Private Network has become one of the core components in large enterprises and as a System Administrator you will most certainly stumble upon this technology. There are multiple VPN equipment Vendors, each one with their own features.
One of the things that all of these providers must agree on is using the same VPN protocols so that communication can be established between different devices. In this article I will show you how to install and configure a VPN Server that uses the PPTP protocol to allow connections from remote clients. PPTP is one of the older protocols introduced with VPN servers and should be starting point when talking about VPN connections.
For this demonstration I will be using a Windows Server 2012 Virtual Machine hosted on my VMware testing lab. Note that the VPN server must be joined in an Active Directory domain and should have at least two network adapters to simulate a real production environment. With VMware, you can easily add or remove network adapters so I recommend using this virtualization product.
Login on the server and open up the Server Manager console. Navigate to the Roles section and click on Add Roles and features.
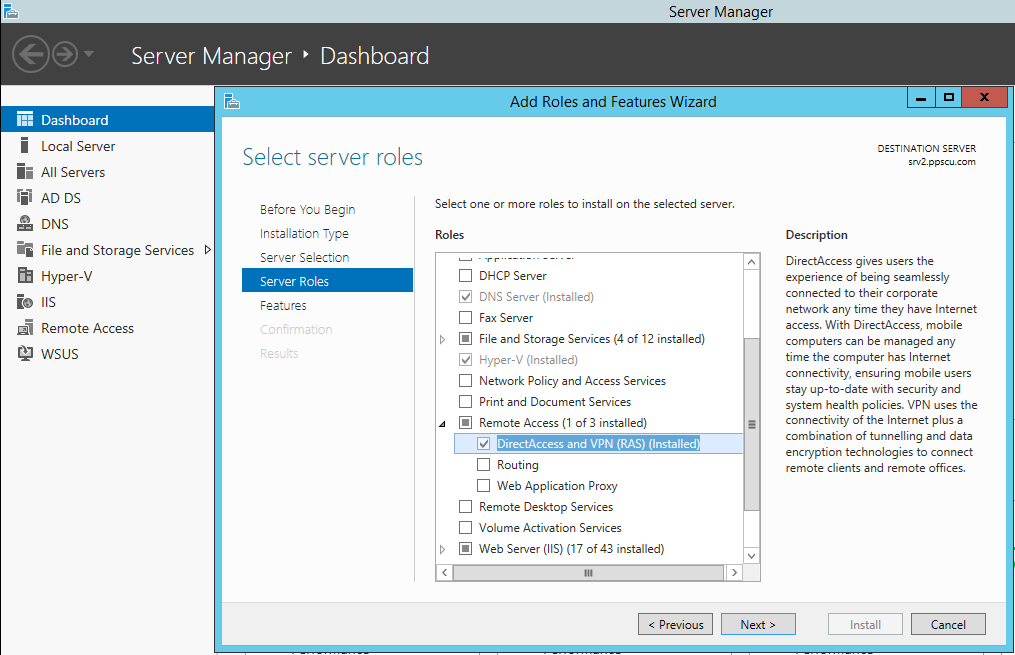
The Add Roles and Features Wizard will start. From the available roles list, select Remote Access and make sure DirectAccess and VPN (RAS) are selected. Note that the install procedure takes a while so please be patient until it’s completed. Once the role has been installed, it will appear in the Server Manager console along other roles installed on the Server.
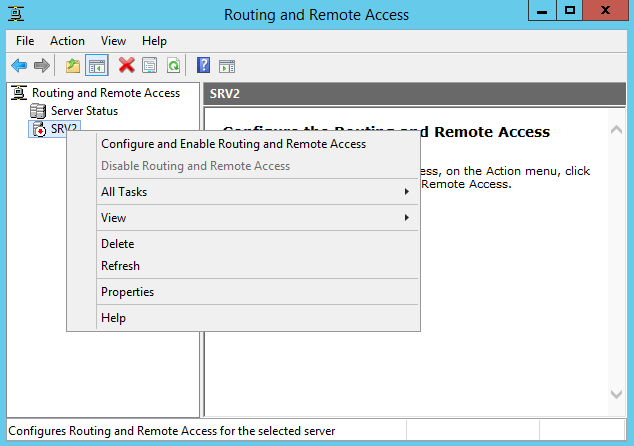
Now it’s time to configure our VPN Server to allow incoming connections using the PPTP protocol. From Administrative Tools open the Routing and Remote Access console. Right click the Server’s name and select Configure and Enable Routing and Remote Access:
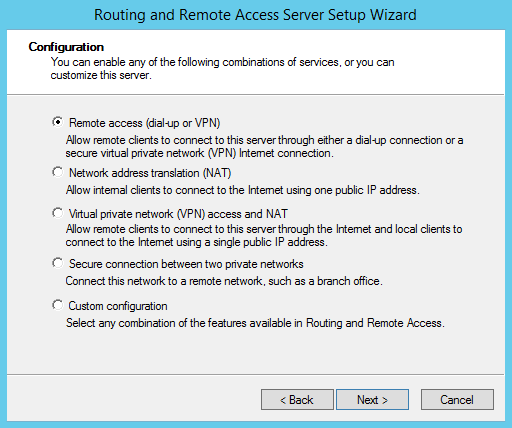
Read the welcome page and proceed to the next section. From the following list select Remote access (dial-up or VPN) and click on the Next button. With this feature enabled you can allow clients to connect to your server using either a dial-up connection or a secured VPN Internet connection:
Dial-up is a technology that’s not widely used anymore because it offers a low bandwidth and is not reliable for a production environment. For this reason we will install only the VPN service on our server, make sure to select it before proceeding further:
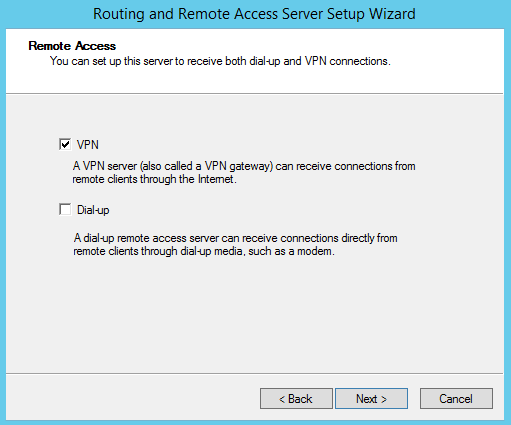
To enable VPN clients to connect to your server you will need to have one interface facing the public network either directly or using a device with NAT activated. For testing purposes I’ve added a second network device on which we’ll assign a public IP to simulate a real environment:
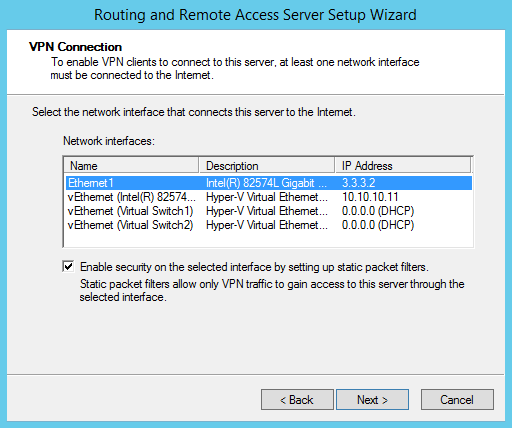
In the next section we’ll need to select the interface that’s connected to the internal network:
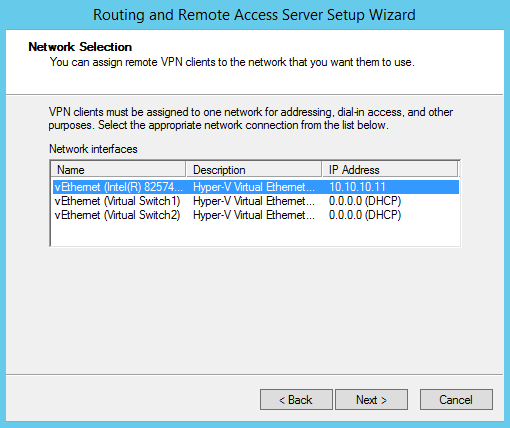
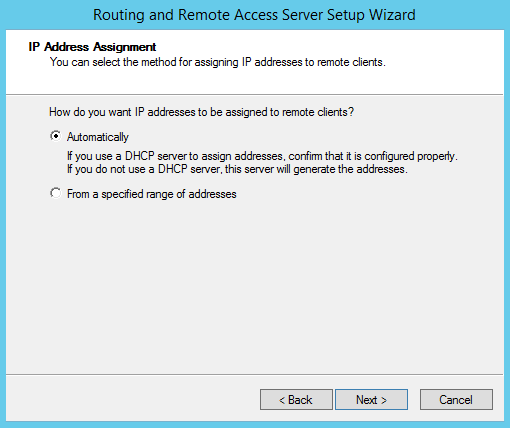
Remote VPN clients can be assigned IP addresses automatically using a local DHCP server or from a predefined range of addresses. I will select the first option and add my DHCP server:
We are using only one Remote Access Server so there is no need for centralized authentication servers. So, I will select the first option from the following section. Large enterprises that use multiple RAS servers use RADIUS servers for centralized authentication:
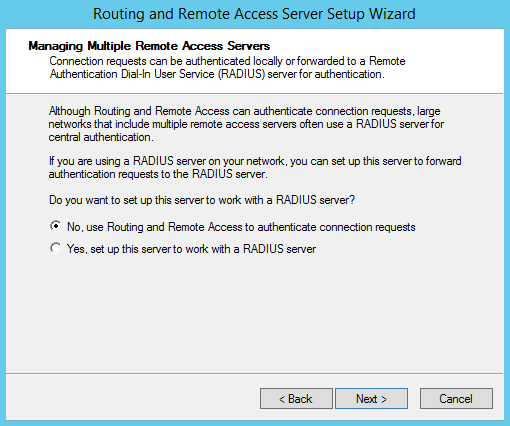
Once the operation is completed, the RAS service will start and clients will be able to connect. The server will have 128 ports configured to allow connections using either IKEv2, SSTP, PPTP or L2TP. The VPN protocol is automatically chosen based on the way the connection is established. For example, if you are using client-server certificates for your VPN connections, the appropriate VPN protocol will be chosen. For IKEv2 you will also need to install Web Server (IIS) role besides the Active Directory Certificate Services.
Note that PPTP protocol is usually used with older non-Microsoft clients and it’s not widely used anymore since a lot of security vulnerabilities were discovered. PPTP connections can be authenticated using MS-CHAP, MS-CHAPv2, EAP and PEAP.
Between these authentication protocols, only EAP offers the most secured connections. PPTP offers support for data confidentiality but not for integrity or origin authentication. The protocol used to encrypt data on PPTP connections is MPPE (Microsoft Point-to-Point Encryption and uses either a 128, 56 or 40 cypher key length.) Authentication protocols can be chosen from the VPN Server properties menu:
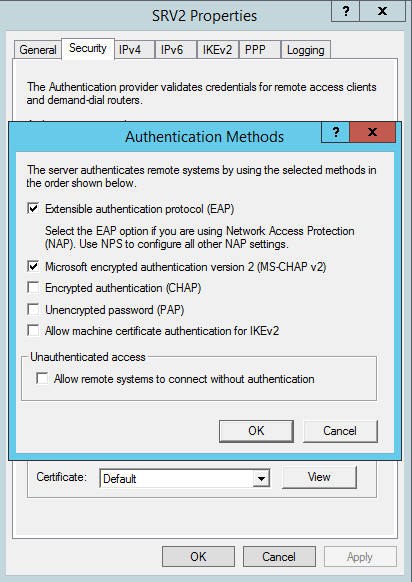
That’s about it for this article folks, hope it has helped you set up remote access servers. As you’ve seen from this article, setting up a Microsoft VPN Server is pretty easy and offers a lot of features. I recommend you always use the strongest authentication mechanism possible to ensure that your private data is kept safe. EAP-TLS should be deployed in large enterprises, but for this technology you’ll need several roles and features configured. If you have any questions, please use our comments area below and I will respond as soon as possible. Wish you all the best and have a pleasant day!
