Introduction
Security is vital for protecting company assets and data subjects. Evolving data protection regulations, like the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), have thrown light on security breaches and the security architecture of those compromised. In 2019, the global average cost for a data breach was $3.9 million![]() , not including reputational damage and hidden costs. Hardening Windows Server 2019 can reduce your organization’s attack surface, minimizing the disruption of business processes, legal and financial repercussions, and other damages. Windows Server comes with a suite of tools that can help defend your infrastructure.
, not including reputational damage and hidden costs. Hardening Windows Server 2019 can reduce your organization’s attack surface, minimizing the disruption of business processes, legal and financial repercussions, and other damages. Windows Server comes with a suite of tools that can help defend your infrastructure.
New Features
Windows Server 2019 showcases several new features:
- Windows Defender Advanced Threat Protection (ATP): hunts and stops low-level malicious processes
- Security with Software Defined Networking (SDN): enhancements include network encryption, firewall auditing, virtual network peering, and egress metering
- Shielded Virtual Machines improvements: fallback HGS (Host Guardian Service) and offline mode aid in redundancy and connectivity, and enabling VMConnect Enhanced Session Mode and PowerShell Direct make troubleshooting easier.
- HTTP/2 for a faster and safer Web: increases throughput and builds stronger connections via encrypted channels
These features should be used in concert with baseline measures, some of which are outlined below, and within an overall security governance program.
Hardening Windows Server
Below are a handful of steps you can take to strengthen the security of your server. These steps cover a wide range of settings from organizational measures to access controls, network configuration, and beyond.
- Conduct a threat risk assessment to determine attack vectors and investments for mitigation strategies.
- Protect your administrative and system accounts with strong passwords.
- Disable unnecessary services and remove unused Windows components.
- Password protect the BIOS/firmware to prevent unauthorized changes to the server startup settings.
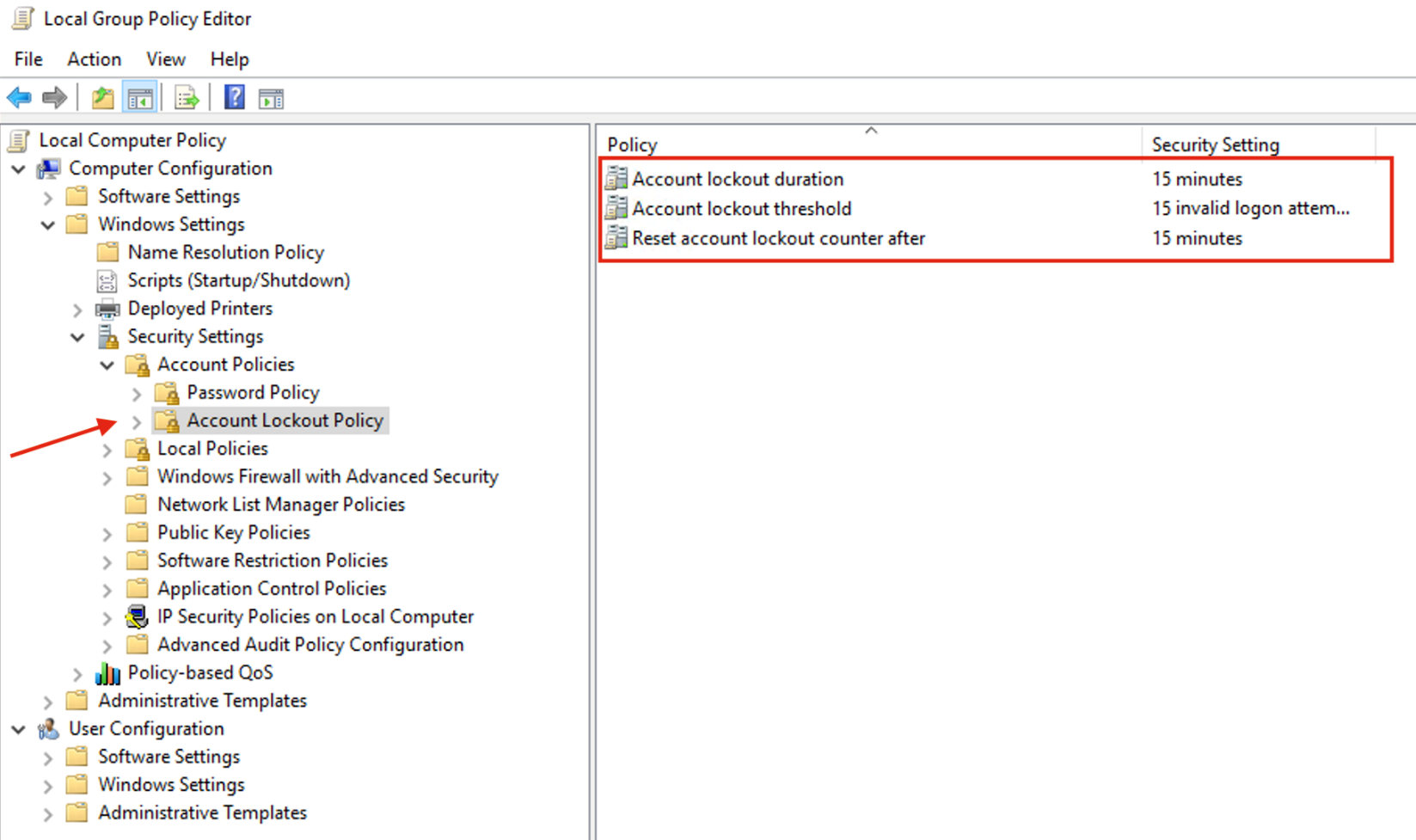
- Configure Account Lockout Group Policy that aligns with best practices.
- Perform SQL server monitoring
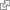
Figure 1: Path to set lockout periods via the Group Policy Editor
- Obey the principle of least privilege by limiting the number of administrators. This is key, as penetration testers and malicious attackers love to use excessive privileges to their advantage.
- Follow privilege access management (PAM) best practices; e.g., only use administrative accounts to perform administrative tasks, and auto-rotate passwords on check-outs and check-ins to mitigate pass the hash attacks
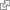 .
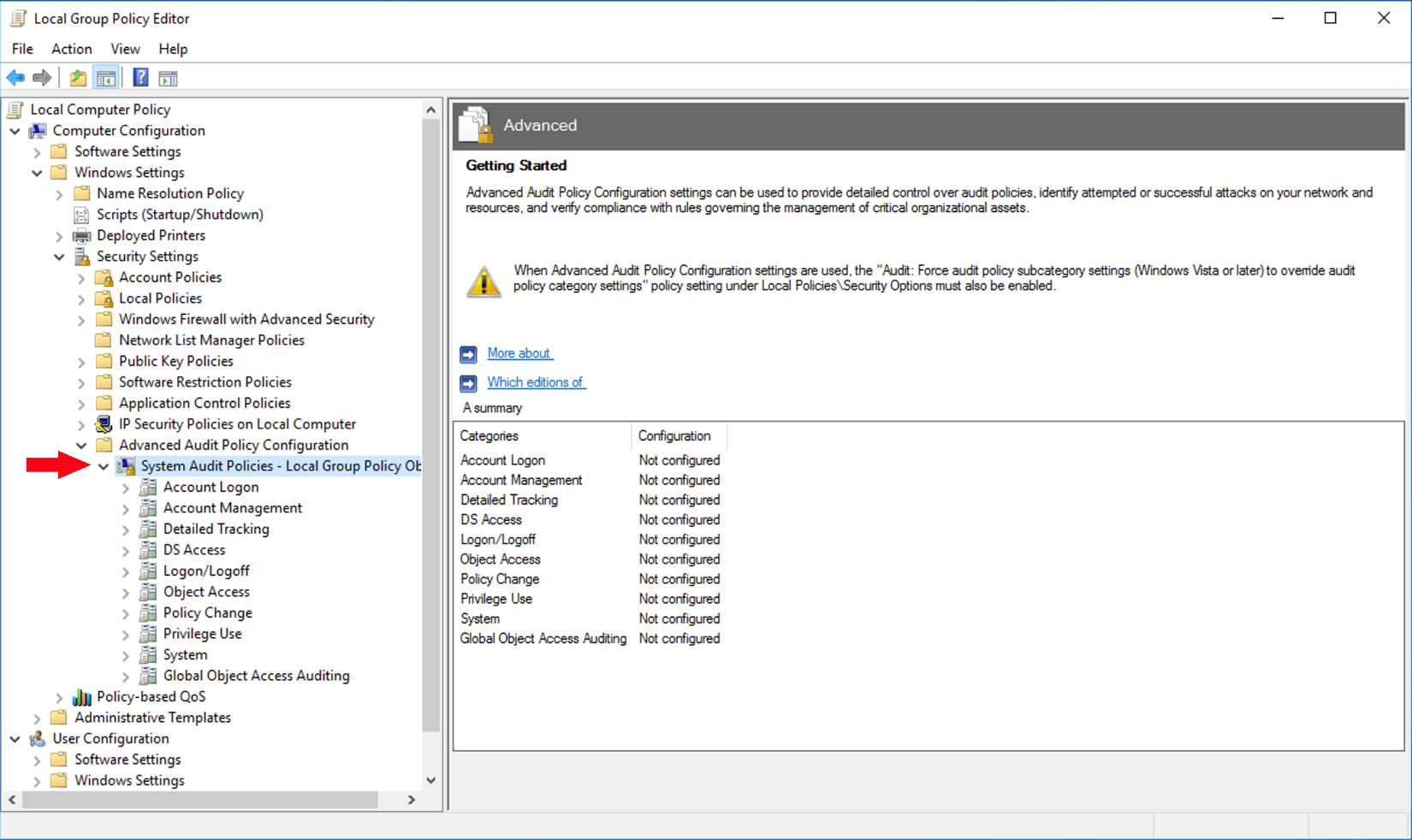
. - Enable Audit Policy to spot mysterious and malicious activity, uphold accountability, and gather forensic data.
Figure 2: Setting up Audit Policies
- Install and activate anti-spyware and anti-virus software, and keep them up to date.
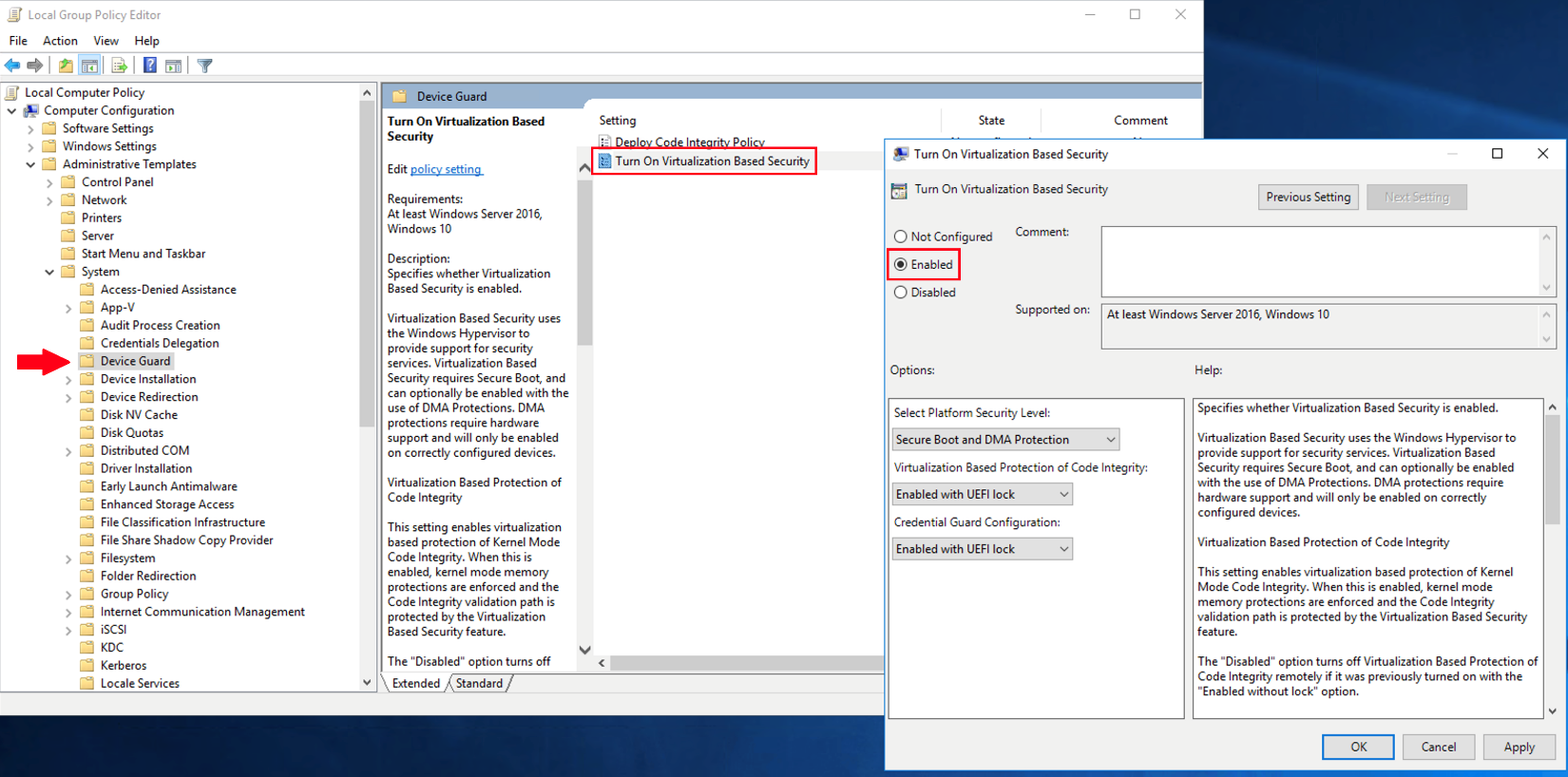
- Enable Windows Defender Credential Guard
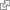 and Windows Defender Exploit Guard for improved hardware security, virtual security, protection against advanced persistent threats (APT), and other benefits.
and Windows Defender Exploit Guard for improved hardware security, virtual security, protection against advanced persistent threats (APT), and other benefits.
Figure 3: Enabling Virtualization Based Security
These tips, while not exhaustive, are a good start. Comprehensive lists for securing Windows Server will be included in the Resources section at the end of this article. Be sure to follow the inline links throughout for further information.
Conclusion
Windows Server 2019 offers several improvements to its security. Such improvements should be implemented on top of fundamental controls, which should in turn be a part of a grander information security program. Ensure these improvements go through a change management process to guarantee proper configuration and a smooth rollout.
Resources
- The Electronic Frontier Foundation’s threat modeling framework
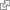
- Windows Server 2019 OS hardening – a blog
 by Thomas Jung
by Thomas Jung - Windows Server 2016 Security Guide
 from Microsoft
from Microsoft - Microsoft Windows Server 2019, Ver 1, Rel 3 Checklist
 Details from NIST
Details from NIST
—–
Paul Margiotis![]() (@paulmargiotis) is the Security Engineer at SentryOne
(@paulmargiotis) is the Security Engineer at SentryOne![]() , where he writes and implements security policy, directs compliance with data privacy and protection regulations, and strengthens the organization’s network and perimeter defense. In his articles, he shares insight into hardening systems and infrastructure, building robust processes and protocols to enhance security governance, risk management, and cryptography. Paul holds a Master’s degree in Cybersecurity, with a concentration in Network Security, from the University of North Carolina at Charlotte.
, where he writes and implements security policy, directs compliance with data privacy and protection regulations, and strengthens the organization’s network and perimeter defense. In his articles, he shares insight into hardening systems and infrastructure, building robust processes and protocols to enhance security governance, risk management, and cryptography. Paul holds a Master’s degree in Cybersecurity, with a concentration in Network Security, from the University of North Carolina at Charlotte.