by Des Nnochiri
 The use of mobile devices as endpoints for corporate and public networks continues as a prevailing trend, putting an emphasis on the need for readily available internet connections and data-processing capabilities.
The use of mobile devices as endpoints for corporate and public networks continues as a prevailing trend, putting an emphasis on the need for readily available internet connections and data-processing capabilities.
Together with the growth and evolution of the so-called Internet of Things (IoT), with its consumer and industry/infrastructure-level ecosystem of widely dispersed, “smart”, and connected devices, new patterns and techniques for data-handling and resource provision have had to develop to enable these emerging networks to keep pace with the demands of their user bases.
The Conundrum of Connectivity
The march of technology has seen the development of smaller but ever more powerful devices, hardware components, and software. This evolution means that there’s now less dependence on “command center” style resources like mainframes, in-house application servers, or databases.
As long as a viable internet connection is present and the resources are out there, somewhere, workers today can operate their laptops, tablets, smartphones, and other hardware from home, public spaces, on the road, or anywhere across the globe.
Connectivity is required to provide feedback, timestamps, geolocation, database or software updates, and a host of other functions. It’s gotten to the stage where some devices and a fair proportion of software applications won’t even work properly, unless there’s an active internet connection present.
So with the increased functionality and mobility of today’s devices and software comes a critical flaw![]() : if an internet link goes down, so does the hardware, software, or service.
: if an internet link goes down, so does the hardware, software, or service.
Edge Computing Defined
Traditional models of information and resource handling for corporate networks have relied on a central store of knowledge, skills, and infrastructure – typically in the form of an in-house data center, and local IT staffing.
With the emergence of the so-called “Internet of Things” (IoT), corporate networks have the potential to become even more widely dispersed and fragmented. Smart sensors, wearable devices, laboratory or manufacturing components, and numerous other IoT devices make it possible for the perimeter of today’s enterprise network to be both fluid and interactive.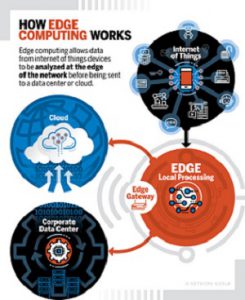
The prevailing characteristic of these IoT devices is their ability to communicate via the internet with their owners/operators, and with information and resources resident in remote locations – be they in the cloud, or at the various sites of an enterprise.
Gartner, Inc. describes edge computing![]() as “solutions that facilitate data processing at or near the source of data generation.” It “serves as the decentralized extension of the campus networks, cellular networks, data center networks or the cloud.”
as “solutions that facilitate data processing at or near the source of data generation.” It “serves as the decentralized extension of the campus networks, cellular networks, data center networks or the cloud.”
Needs Met by Edge Computing
Edge computing has developed to meet the demands of the growing ecosystem of edge devices. It does this by moving processing and computational power to the edges of the network – and therefore much closer to its users. Its remit is to back up and provide power to various remote systems, improving overall security for the enterprise and offsetting the demands of enterprise hardware.
Santhosh Rao, principal research analyst at Gartner puts it this way: “As the volume and velocity of data increases, so too does the inefficiency of streaming all this information to a cloud or data center for processing.”
Edge computing provides an assortment of mechanisms for data processing and resource provision at network perimeters. Solutions run the gamut from basic event filtering, to complex-event processing or batch processing. Deployments may be mobile (as in the case of a smart vehicle or smartphone) or static (e.g. when incorporated into a building management solution, at an offshore oil rig or manufacturing plant).
Practical Applications
A number of complex deployments of edge computing have been put in place, already.
Gateway solutions are possible, such as in a smart vehicle where local data from traffic signals, other vehicles, GPS devices, proximity sensors and the like are aggregated and processed locally, to improve vehicle navigation or safety.
Self-driving or autonomous vehicles![]() require split-second data processing and decision-making – and edge computing allows for this real-time response. As Artificial Intelligence (AI) technology evolves, this is being incorporated into on-board computer systems, to further improve vehicle performance.
require split-second data processing and decision-making – and edge computing allows for this real-time response. As Artificial Intelligence (AI) technology evolves, this is being incorporated into on-board computer systems, to further improve vehicle performance.
The emerging 5G mobile communication networks employ edge servers, which host applications and cache content for local telecoms subscribers. This eliminates the need to send information streams through a potentially congested backbone network.
In some retail outlets and offshore oil rigs, edge servers are being used to form clusters or micro data centers and create pools of computational power which can be used locally.
The Essential Need for Data Centers
This last point demonstrates an important issue: with the emergence of edge computing, there’s now a diversifying role for the data center.
Edge computing is all about moving information and computational resources closer to their end users. In practical terms, this requires making data center and infrastructure resources available at numerous locations around a network’s perimeter. But rather than traditional installations of “big iron”, these edge computing data centers must be more mobile and adaptable in nature.
A number of big players in the cloud sector have recognized this fact, and are offering new services aimed at enabling users to integrate their devices with major platforms such as Google and AWS.
Security Considerations at the Edge
In any discussion involving mobile computing or devices of the IoT, security (and the current lack thereof) usually tends to come up. Edge computing is no exception – and there have already been concerns expressed about the risks involved, and what steps may be taken to reduce them. The security debate![]() is double-edged.
is double-edged.
On the one hand, there’s the possibility that with localized data not having to travel over a public network, edge computing environments are actually safer than those which rely on a centralized data center or cloud service (which could be compromised by a single attack).
On the other hand, edge devices may be inherently vulnerable, a fact that recent breaches of massive numbers of IoT devices have already demonstrated.
In either case, measures such as data encryption (for information in transit and local storage), access control methods, and the use of Virtual Private Networks (VPNs) are advised.