Category: Cryptolocker / Ransomware
-

How to Prevent, Detect, and Remove Spyware
Spyware is a type of malware that hides deep inside your computer. Unlike more visible types of malware, spyware lets you go about your tasks while secretly recording information—especially passwords and other sensitive credentials. Since spyware is difficult to notice, both home users and system administrators need to prioritize its prevention and detection. Thankfully, […]
-

Ransomware: 11 Steps You Should Take to Protect Against Disaster
The frequency and volume of ransomware attacks have increased dramatically in the past few years. Few people in the tech industry will forget the 2017 WannaCry attack, which infected over 200,000 computers in 150 countries worldwide and brought down part of the U.K.’s National Health Service, or the 2019 RobbinHood attack, which brought the Baltimore […]
-

5 Cybersecurity Trends for 2020
The world of cybersecurity is fast-paced and constantly changing. Where certain strategies once worked perfectly, new threats eventually emerge. Keeping up with a growing number of malicious influences and implementing effective security strategies to combat them involves staying up to date on yearly shifts in cybersecurity practices across industries. Here, we have put […]
-

What Level of Anti-Virus Protection Do You Need?
By Des Nnochiri Let’s be honest; the answer to that question is simple. You need the best level, and if time, money, and factor X were not an issue, every computer in the land would be an impenetrable digital fortress. We could redirect that energy towards something more worthwhile, such as brokering world peace, […]
-

The Sound of Silence: Threats from Without and Threats from Within
By Des Nnochiri Recent news has broken about a group of hackers which appears to be operating out of Russia. The group, dubbed “Silence,” is believed to be involved in the theft of over $800,000 from multiple Russian and Eastern European financial institutions. However, what is particularly notable about this group is they […]
-

How to check for MS17-010 and other HotFixes
Sometimes you need to check on the status of your applied updates and quickly. With news of the WannaCrypt/WannaCry Ransomware spreading via the MS17-010 vulnerability around the globe it’s a good idea to double check that all your updates are applied correctly. The following is a quick PowerShell Execute Script monitor that you can add […]
-

5 Great Ransomware Removal Tools
Ransomware is one of the fastest growing security threats in the online world. Over the last few years, ransomware attacks have become increasingly common to the extent that these attacks have evolved into one of the most harmful forms of cyber attack there is. Ransomware attacks can target any PC user, whether it’s a […]
-

What is Cryptolocker Ransomware?
Cryptolocker is a well known malware (software that does harm) of a particular variety: ransomware. Some malware (like computer viruses) delete and destroy. The hackers that create ransomware have other motivations: money. Ransomware Ransomware does something to your computer, and then demands a ransom payment to get your computer back to the way it used […]
-
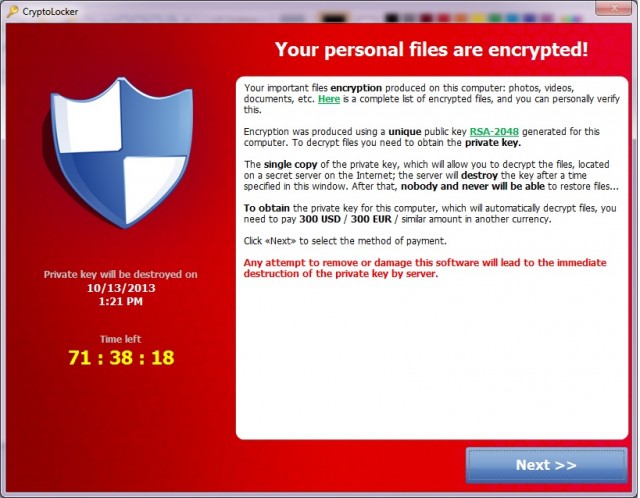
Early Detection and Prevention of CryptoLocker
In case you haven’t heard, CryptoLocker is a popular form of the ransomware malware that encrypts your files and then holds them hostage. Generally you have to pay to get them decrypted. If you have a backup of all of your data, you might be able to avoid the payment. If you have a backup… […]
-
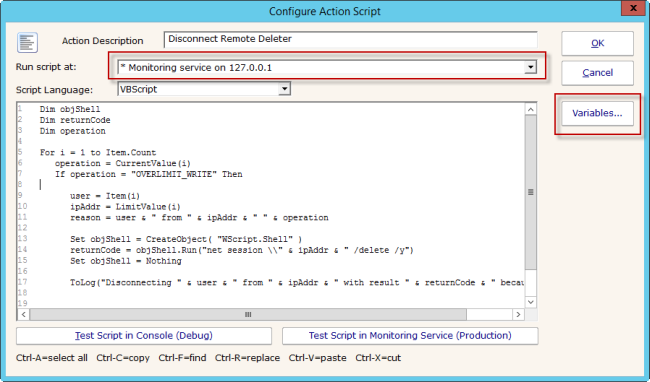
Early Detection and Prevention of CryptoLocker – The Response Scripts
In the previous post, I mentioned a couple of ways customers are working on detecting CryptoLocker attacks. In this post, I’ll share a few scripts they use in response. Ideally, you could quarantine the user’s computer from where the attack is coming from. In practice, that can be tricky. Note that these responses could be […]