By Des Nnochiri
Internet of Things (IoT) security ranks as a major concern for many enterprises. A 2018 survey of over 600 IT decision-makers worldwide conducted by 451 Research found that 55% of those polled rated IoT security as their top priority. It’s easy to see why.
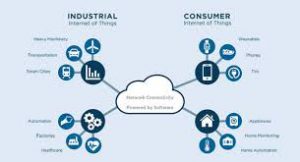
As well as any “smart, connected” devices deployed by an enterprise to enhance its own operations, many organizations also have to contend with the presence of consumer-grade hardware such as smart watches, fitness trackers, smart speakers, and other devices brought in by employees. These devices may piggyback onto corporate internet connections and wireless networks—often without the knowledge or oversight of IT and security personnel.
Security Challenges Posed by the IoT
The Online Trust Alliance (OTA), an initiative of the Internet Society, has identified a number of key areas of concern regarding unregulated and/or poorly-configured devices of the IoT. These include:
- Simple or non-existent user interfaces, making it hard for users to access or configure IoT devices.
-
Use of default (or hard-coded) passwords, which are easy for attackers to guess or hack.
-
Open hardware and software ports for IoT devices, introducing network vulnerabilities.
-
Limited local password protection.
-
Devices which lack the ability to be updated.
-
IoT components that “phone home” frequently, leaving their communication streams vulnerable to interception.
-
Devices that collect more data than expected and use unsecured backend services.
Enterprise Roles for the IoT
In the face of these risk factors, organizations might be forgiven for shunning the use of IoT in their operations altogether. However, there are benefits to be gained from the use of IoT devices and connectivity by an enterprise.
By tapping into the massive amounts of data that connected devices generate, organizations can exploit the IoT ecosystem to better track and monitor marketing and customer relationship functions, inform business decisions, improve utilities, save energy and physical resources, and increase business efficiency.
So there’s a big incentive for commercial organizations to plug the existing and potential security gaps that their IoT investments may produce, so as to maximize their benefits. This may be accomplished on a number of fronts.
Asset Discovery and Risk Assessment
These are high-sounding terms for what are essentially logical and straightforward processes:
1. Finding out what IoT devices and services are currently being used by your organization, both officially and informally.
2. Determining the risks they pose to your operational integrity, cyber security levels, and links or relationships with external agencies and third parties.
Everything with an IoT connection should be documented, and all devices and network connections should be examined for open ports, possible weaknesses, and security vulnerability “back doors” that might give hostile intruders access to the system.
Management and Monitoring of Endpoints
Part of the attraction of an IoT deployment is its reliance on edge computing and the shifting of network administration and provisioning tasks to positions much closer to the devices that need to be served. This enables workers in the field to benefit from on-the-fly connections to information and resources.
This approach also greatly increases the number of endpoints associated with an enterprise network. Much of the challenge of securing this ecosystem lies in the effective management and monitoring of the multiple endpoints.
Cyber security experts recommend![]() the use of “security gateways”, which are checkpoints set up at the network perimeter to enable an organization to inspect, audit, and control communications into and out of the network. These may involve dedicated hardware, security software, and network management protocols set up in accordance with the organization’s own security policy.
the use of “security gateways”, which are checkpoints set up at the network perimeter to enable an organization to inspect, audit, and control communications into and out of the network. These may involve dedicated hardware, security software, and network management protocols set up in accordance with the organization’s own security policy.
Software-defined network perimeters may be constructed to hide IoT connections from the public internet. Here, client software must verify IoT device identities (a process called pre-authentication) and user identities (a process known as pre-authorization), before access is granted to an application layer.
Network Segmentation
Breaking a network into separate and individually managed sections has always been a fundamental security strategy, and for systems incorporating IoT devices this approach remains an effective one.
The Online Trust Alliance (OTA) recommends![]() that all IoT devices should be confined to a separate network, which can be monitored and firewalled to meet the specific threats that they face. This will allow for the policing of incoming traffic, the profiling of traffic to identify anomalies, and the prevention of dangerous crossovers to the core network.
that all IoT devices should be confined to a separate network, which can be monitored and firewalled to meet the specific threats that they face. This will allow for the policing of incoming traffic, the profiling of traffic to identify anomalies, and the prevention of dangerous crossovers to the core network.
Ongoing and Dynamic Remediation
IoT technology is still in its relative infancy, and new security vulnerabilities and quirks are being discovered all the time. This imposes a need to continuously monitor vendor websites and threat intelligence databases for the latest developments, and to apply any updates and security patches as soon as they become available.
The asset discovery and inventory of IoT devices which I mentioned previously will assist in identifying which hardware and systems require patching or remediation.
Don’t Forget the Basics
Hard-coded and default passwords associated with IoT devices have already been a source of great joy to hackers, who have been able to exploit the lax security of unconfigured hardware in staging Distributed Denial of Service (DDoS) attacks![]() capable of taking down major portions of the internet.
capable of taking down major portions of the internet.
As far as is possible, default passwords and settings for IoT devices should be changed as soon as they’re acquired. Passwords and access codes should also be changed regularly. Of course it’s never a good idea to use the same passwords across multiple accounts or devices.
Test Before Deploying
Penetration testing![]() involves the employment of benevolent or “white hat” hackers to stage real-time and real-world attacks on a system to establish how secure it is (or not). These kinds of tests—which may be performed by trusted external contractors—should be performed on any IoT hardware that you intend to include within your network. At the very least, before these devices are deployed in practice.
involves the employment of benevolent or “white hat” hackers to stage real-time and real-world attacks on a system to establish how secure it is (or not). These kinds of tests—which may be performed by trusted external contractors—should be performed on any IoT hardware that you intend to include within your network. At the very least, before these devices are deployed in practice.
Occasional testing may be ordered once the systems are online to give insight into how your organization’s IoT deployment performs over time.
Don’t Forget the Users
As with any security policy, buy-in and personal involvement from the people in your organization are essentials for success. So it’s vital to take the necessary steps to keep stakeholders informed about policy matters and to provide regular sessions of security awareness training to instill a culture of cyber security and to foster best practices.
Plan for the Inevitable
Finally, accept the wisdom that data breaches or security incidents will inevitably occur, no matter how many precautions you take. Equipping and training an incident response team and providing clear guidelines for how your people should respond to incidents and alerts will help minimize the impact of security incidents on your IoT deployment.