Part 2, Continued from “How to Configure a Public Key Infrastructure on a Windows Server – Part 1“
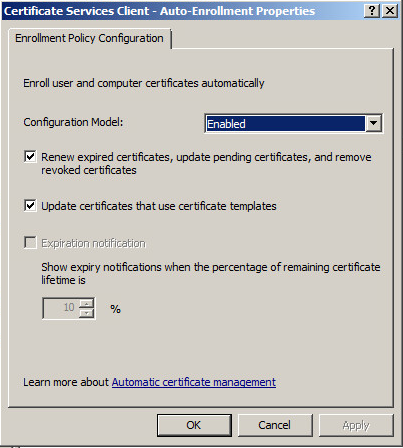
Enable the policy and check the Renew expired certificates, update pending certificates and remove revoked certificates and update certificates that use certificate templates check-boxes:
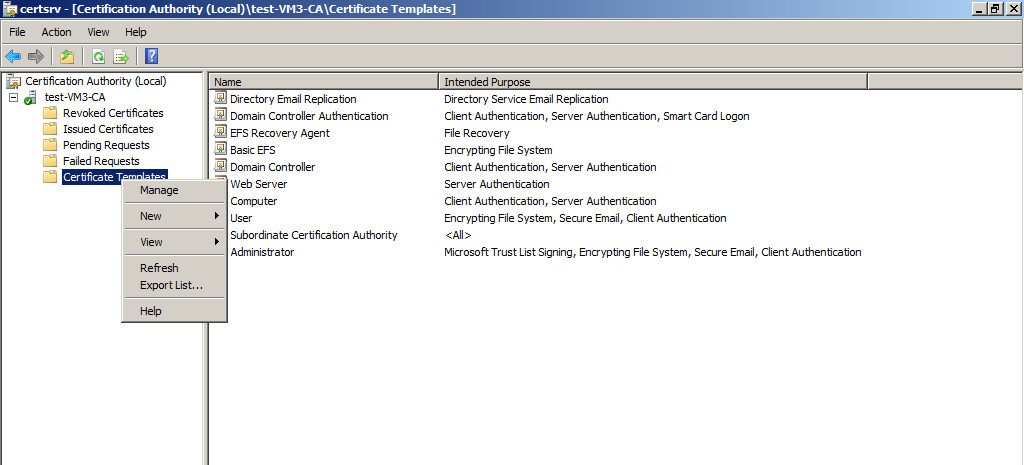
Now we have to configure certificate templates for auto-enrollment. Open the Certification Authority console, navigate to the Certificate Templates section, right click and select Manage:
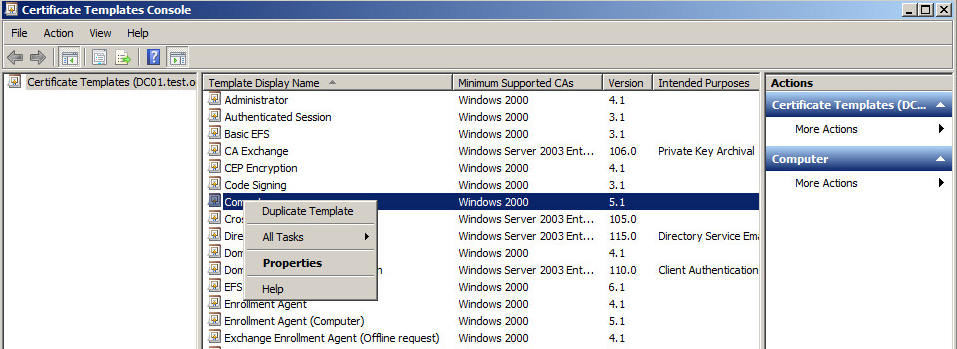
From the Certificate Template section right click the Computer template and select Properties:
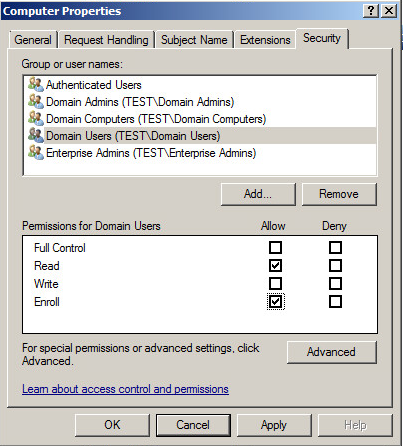
Navigate to the Security tab and add the users or security groups that will be able to enroll these certificate types. I’ve added the Domain Users group and set the Read and Enroll permissions:
We’ve finished the CA auto-enrollment configuration. Remember that all wireless clients must trust this CA in order to request and renew certificates. Because we’ve deployed the PKI within our Active Directory Domain, all machines will receive a certificate for the CA in the Trusted Root Certification Authorities:
After configuring the CA, you’ll need to configure the RADIUS server for this authentication type and all your wireless computers will be able to authenticate using certificates.
That’s it for this article folks, hope you’ve enjoyed it. If any of this is unclear, please post any questions and we will respond as soon as possible. Don’t forget to rate this article and share it to others. Enjoy your day and stay tuned for following articles.