In this article I will show you how to use Windows Firewall to authorize connections before data can be sent between devices. Authorization offers you an extra security layer and should be used whenever possible. There are services or applications that include authorization rules so that only allowed users/computers can connect to certain network resources. Applications like IIS or Windows sharing offer different authorization types. Authorization should be the first security layer used to protect private information against external security threats.
Let’s open up the server manager console and navigate to Windows Firewall with Advanced Security section. Note that for this demonstration I will be using a Windows Server 2012 R2 machine, but similar settings are applicable to Windows Server 2008 versions. Once you’ve openned the console navigate to Outbound Rules:
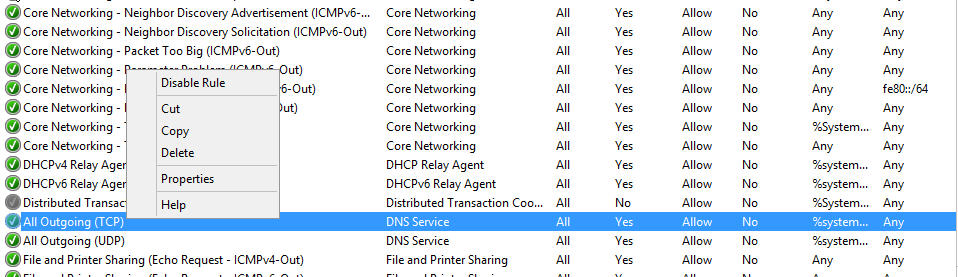
If desired, you can configure a new outbound rule which will filter the traffic based on the specified criteria. I will be editing the All Outgoing (TCP) rule which is responsible for managing all outbound connections that are using a TCP port. Right click this rule and select Properties:
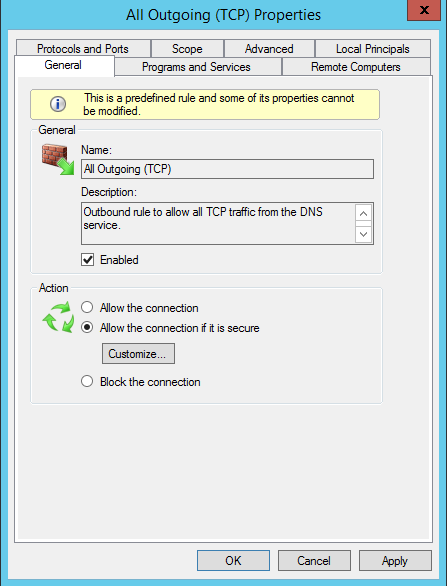
From the General tab select allow the connection if it is secure and click on customize. This option will allow outbound connections only if they are secured:
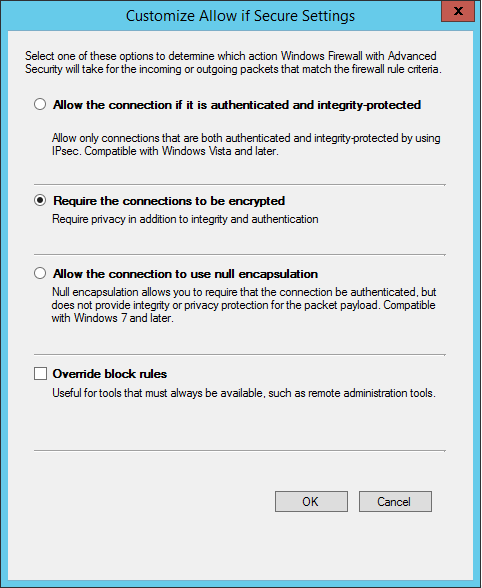
There are several options available when allowing secured connections only. Note that authorization takes advantage of IPSec when filtering rules so, you can require authentication, integrity and/or encryption. When enabling require the connections to be encrypted, besides data integrity and authentication, privacy will also be used:
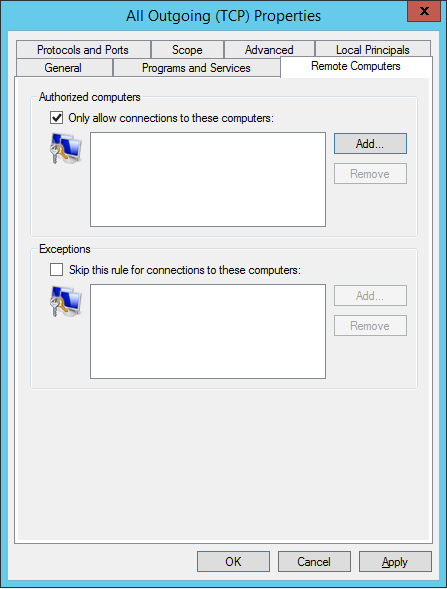
Once you press OK, navigate to the Remote Computers tab to add the authorized computers that will take advantage of this rule. You can enable authentication for individual or a specified group of computers. The rule will then be applied for outbound connections and only for the machines added in this section. We can also configure exceptions for particular hosts or group of computers. This basically means that for the specified hosts, the rule will not be applied and these computers will not be authenticated:
Based on the criteria configured in this section, the rule will filter any outbound packets. If a match for this rule is found then the computers will be checked for authorization. If the machines were not added within this section, the connections will be dropped.
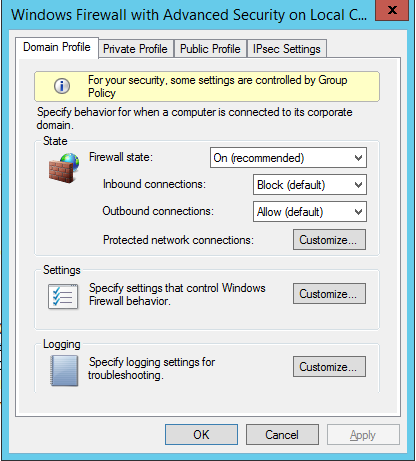
For monitoring network traffic you can enable logging on your Windows Server so that you can troubleshoot and visualize authentication requests. Right click Windows Firewall with Advanced Security and select Properties. There are multiple sections available based on the location of your workstations. Because I’m using an Active Directory domain, I will enable logging on the Domain Profile. From the Logging section select Customize:
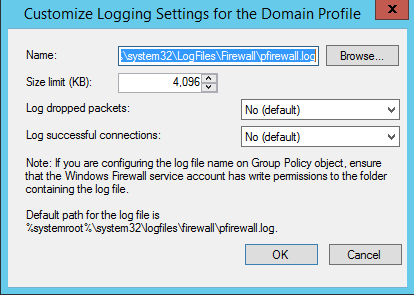
You’ll need to specify the name and location of the log file, size limit and if the server will log dropped packets or successful connections:
Logging outbound or inbound connections offers you a way to troubleshoot and monitor server’s connections. If there are malicious users trying to authenticate using your server you can also block connections based on the logged IP addresses.
That’s it for this article folks, hope you’ve understood the basics of using Windows Firewall to authorize connections. If you have any questions don’t hesitate to post a comment and we will answer as soon as possible. Enjoy your day and stay tuned for the following articles.
Image credits: By Berishafjolla (Own work) [CC-BY-SA-3.0 (http://creativecommons.org/licenses/by-sa/3.0)], via Wikimedia Commons