Month: September 2014
-

How to Install & Configure Remote Access Servers
VPN or Virtual Private Network has become one of the core components in large enterprises and as a System Administrator you will most certainly stumble upon this technology. There are multiple VPN equipment Vendors, each one with their own features. One of the things that all of these providers must agree on is using the […]
-

Shellshock vulnerability – worse than HeartBleed 🙁
Do you remember HeartBleed from a few months back? There’s another huge vulnerability that just came to light: Shellshock. And this one is much worse than HeartBleed 🙁 Shellshock is based on a vulnerability in the Unix/Linux bash command processor. Bash can be forced to execute commands stored as ‘environment variables’ and unfortunately, many programs […]
-

Managing Your Twitter Account
Twitter can be confusing especially for those new to social networking. There are lots of things to consider: Whom do I follow? What do I tweet? What on earth are hashtags? Finding the answers to these questions can take a bit of trial and error before you get into the swing of things, but, when […]
-
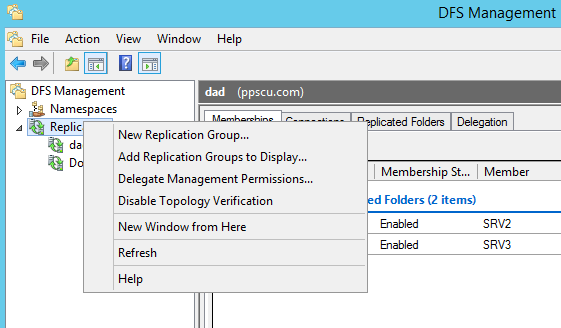
How to Configure DFSR Replication
We’ve talked in a previous article about DFS namespace and we’ve seen how to install and configure this feature on two Windows Server 2012 machines. Now that we’ve configured our DFS namespace it’s time to enable DFS Replication and allow file transfer between servers. Note that by now you should have two Windows Server 2012 […]
-
How to deploy a new VM on Hyper-V
Now that we’ve seen how to install and configure Hyper-V Server role on our Windows Server 2012 machine, it’s time to deploy a new Virtual Machine using our virtualization product. Note that by now you should have a Windows Server 2012 running Hyper-V. If you haven’t read the last article please read it here before […]
-

Big Data and the Law
Big Data is the term used to describe the commercial aggregation, mining, and analysis of very large, complex and unstructured datasets based on social media and Web-enabled workloads. Platforms like Google and LinkedIn have created a revenue stream from the data they collect. Everything from your Facebook posts and tweets, to your late-night shopping habits […]
-

Infographic: Google+ or Facebook for your Business?
It is a debate that has been going on for years, which is better for business, Facebook or Google+? In past blogs the answer had always come down to one thing … audience. And in that specific competition Facebook wins hands down. It is true, as the most popular social network, Facebook, has held the […]